Cybersécurité dans l'espace: comment Thales relève les défis à venir
North America News

New Xiū gǒu phishing kit targets users in five countries with 2,000 fake sites
A new phishing kit called Xiū gǒu is being used in attacks targeting users in Australia, Japan, Spain, the United Kingdom and the United States since September 2024. With more than 2,000 identified fake websites, Xiū gǒu targets sectors such as utilities, messaging, banking and digital services. Cybercriminals employ the kit to deploy phishing sites that use Cloudflare’s anti-bot and hosting protection, making them difficult to detect. The kit, developed by a Chinese-speaking actor, uses technologies such as Golang and Vue.js and is designed to exfiltrate credentials via Telegram. The attacks are distributed via Rich Communications Services (RCS) messages, which alert about parking tickets or package delivery issues, encouraging victims to click on shortened links to resolve the supposed problem.

KillNet launch a new campaign against the United States
The two pro-Russian hacktivist groups KillNet and KillMilk announced on 5 October on their communication channels that they are preparing a large-scale attack and disruption campaign targeting the United States. Targeted are government tax payment sites, state websites in Alabama, Alaska, Colorado, Connecticut, Delaware, Florida, Hawaii, Idaho, Indiana, Kansas and Kentucky. This campaign may be the beginning of the anti-American operations announced by killnet in recent months, which are expected to take place after they have gained momentum. An attack on so many computer resources at once will require more manpower and technical power than KillNet's usual operations. It is therefore likely that the group has indeed made the progress it said it would and that its fundraising campaigns have paid off. October may well mark the start of its new operations, which could last for several months, in parallel with Russia's geopolitical statements. These simultaneous attacks, if real, will have a large-scale impact on a large number of states and will therefore be difficult to counter at the federal level. They are therefore likely to have an impact and prevent the government from providing its usual services for an indefinite period of time. Because an attack of this magnitude is resource intensive, it is possible that the attack campaign will be very limited in time. Read more about it : here

Microsoft disrupts a Russian group's cyber-espionage campaign
The Microsoft Threat Intelligence Center (MSTIC) has observed and taken actions to disrupt campaigns launched by SEABORGIUM, an actor Microsoft has tracked since 2017. SEABORGIUM is a threat actor that originates from Russia, with objectives and victimology that align closely with Russian state interests. Its campaigns involve persistent phishing and credential theft campaigns leading to intrusions and data theft. SEABORGIUM intrusions have also been linked to hack-and-leak campaigns, where stolen and leaked data is used to shape narratives in targeted countries. While we cannot rule out that supporting elements of the group may have current or prior affiliations with criminal or other nonstate ecosystems, MSTIC assesses that information collected during SEABORGIUM intrusions likely supports traditional espionage objectives and information operations as opposed to financial motivations. Read more about it : here
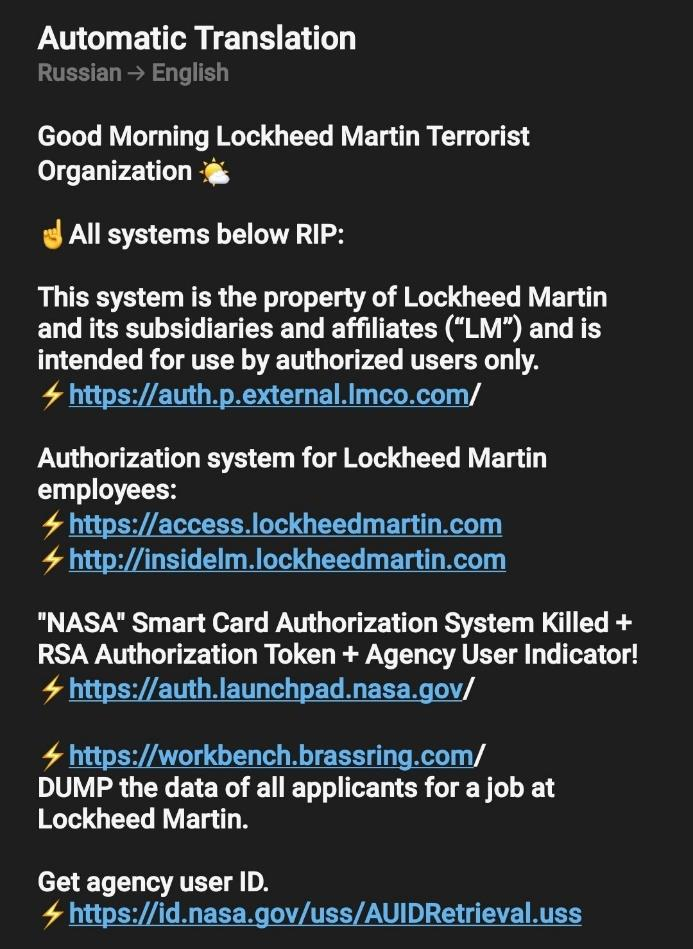
KillNet continues cyber attack on US senate and KillMilk claim attack on LockHeed Martin and NASA
The pro-Russian group KIllNet announced on 10 August on its telegram account that it was continuing its DDoS attack against the US Senate streaming site, which began on 9 August. In parallel, former leader KillMilk shared images of what he claims is the start of his attack on the Lockheed Martin site. Read more about it : here
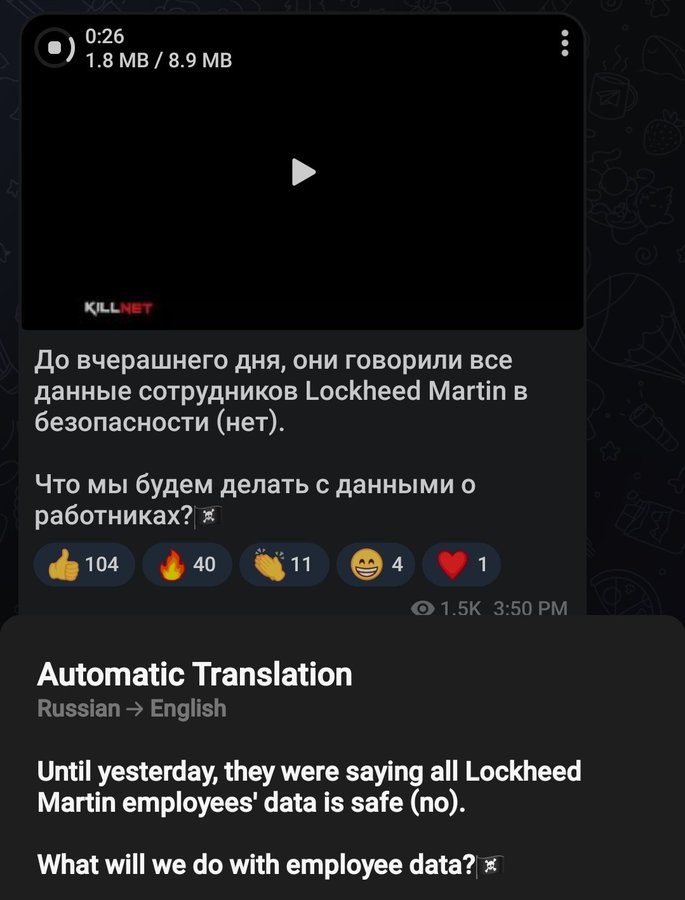
KillNet and KillMilk pro-Russian hacktivists posted Lockheed Martin data
The pro-Russian group KillNET, posted claims to have carried out a data theft attack on the LockHeed Martin website alongside KillMilk. They posted on their Telegram channel: "Until yesterday, they said all LockheedMartin employee data was secure. The message was accompanied by a list of credentials that may have been collected from known data breaches. Killmilk also shared a video showing these same names and other PII allegedly from Lockheed Martin. It is possible that this stolen data is just subversion to make it look like a successful attack, but that the data in question is just old data recovered from other open source Leak sites. Read more about it : here

Killnet and Killmilk continue to threaten Lockheedmartin
The pro-Russian hacktivist group KillNet and its former leader KIllMilk continue to claim responsibility for attacks on the US company Lockheed Martin. In their latest communiqués on their Telegram channels, KillMilk and Killnet announce that Lockheed Martin's share price has fallen and lost value as a result of their offensive actions even though none of the data they claimed to have stolen has been revealed. Read more about it : here

Leaked Audio From 80 Internal TikTok Meetings Shows That US User Data Has Been Repeatedly Accessed From China
For years, TikTok has responded to data privacy concerns by promising that information gathered about users in the United States is stored in the United States, rather than China, where ByteDance, the video platform's parent company, is located. But according to leaked audio from more than 80 internal TikTok meetings, China-based employees of ByteDance have repeatedly accessed nonpublic data about US TikTok users — exactly the type of behavior that inspired former president Donald Trump to threaten to ban the app in the United States. Read more about it: here

Bridgestone Americas confirms ransomware attack, LockBit reportedly to leak data
LockBit ransomware gang claimed to have compromised the network of Bridgestone Americas, one of the largest manufacturers of tires, and stolen data from the company. The Bridgestone Americas family of enterprises includes more than 50 production facilities and 55,000 employees throughout the Americas. On February 27, some company employees at Bridgestone’s La Vergne plant reported being sent home due to a possible cyber attack. Bridgestone launched an investigation into the incident and hired a prominent consultant firm to understand the full scope and nature of the incident. Read more about it here.
United States leads seizure of one of the world’s largest hacker forums and arrests administrator
The Department of Justice today announced the seizure of the RaidForums website, a popular marketplace for cybercriminals to buy and sell hacked data, and unsealed criminal charges against RaidForums’ founder and chief administrator, Diogo Santos Coelho, 21, of Portugal. Coelho was arrested in the United Kingdom on Jan. 31, at the United States’ request and remains in custody pending the resolution of his extradition proceedings. Read more about it here.
LockBit ransomware gang lurked in a U.S. gov network for months
A regional U.S. government agency compromised with LockBit ransomware had the threat actor in its network for at least five months before the payload was deployed, security researchers found. Logs retrieved from the compromised machines showed that two threat groups had compromised them and were engaged in reconnaissance and remote access operations. The attackers tried to remove their tracks by deleting Event Logs but the pieces of the files remained allowed threat analysts to get a glimpse of the actor and their tactics. Read more about it here.