Bringing cybersecurity globally to critical and complex key activities
Europe News
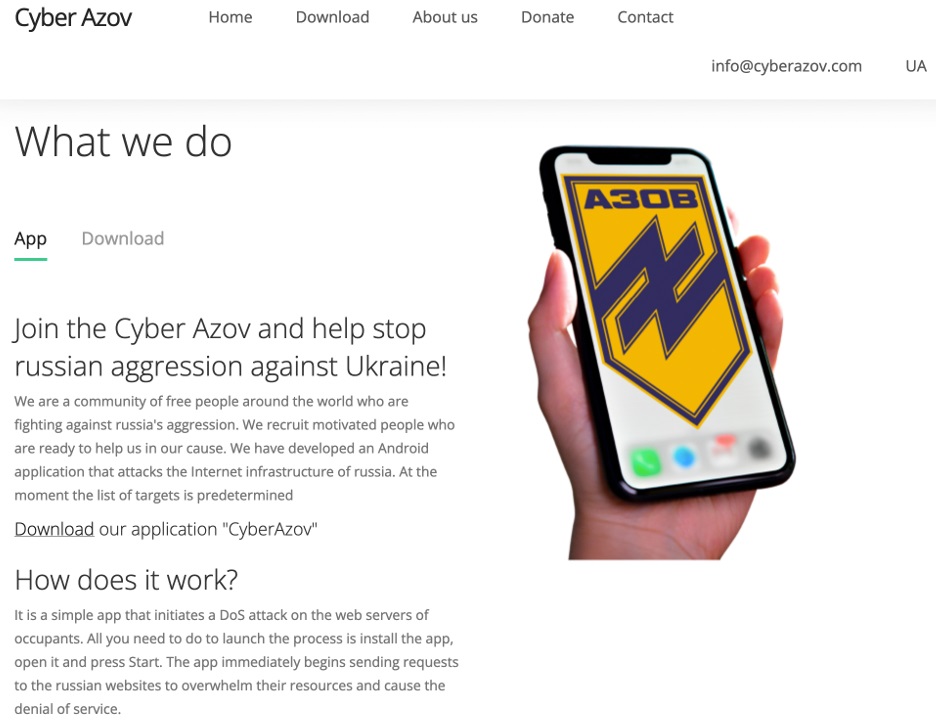
Russian hackers use fake DDoS app to infect pro-Ukrainian activists
Google's Threat Analysis Group (TAG), whose primary goal is to defend Google users from state-sponsored attacks, said today that Russian-backed threat groups are still focusing their attacks on Ukrainian organizations. In a report regarding recent cyber activity in Eastern Europe, Google TAG security engineer Billy Leonard revealed that hackers part of the Turla Russian APT group have also been spotted deploying their first Android malware. They camouflaged it as a DDoS attack tool and hosted it on cyberazov[.]com, a domain spoofing the Ukrainian Azov Regiment. Google TAG's analysts believe Turla's operators used the StopWar Android app developed by pro-Ukrainian developers (hosted at stopwar[.]pro) when creating their own fake 'Cyber Azov' DDoS application. "Join the Cyber Azov and help stop russian aggression against Ukraine! We are a community of free people around the world who are fighting against russia's aggression," the attackers prodded potential targets on the app's download page (still up when the article was published). "We recruit motivated people who are ready to help us in our cause. We have developed an Android application that attacks the Internet infrastructure of russia." Read more about it: here
KromSec has targeted belarus
The pro-Ukraine hacktivist group "Kromsec" claims responsibility for an attack on a Belarusian media website "Belarus.news". The attack is part of a wider campaign of cyber attacks by pro-Ukraine hacktivists targeting Belarus for its support of Russia in the war in Ukraine. Read more about it : here

The data of the union of the Valdisieve and Valdarno Municipalities are online
We had recently spoken of an IT attack on the Unione dei Comuni Valdisieve e Valdarno, but we did not know which cybergang had attacked the union, nor the amount of ransom demanded. But as we have always said, ransomware is 'blatant' and lays bare all truths, even those we would never want to talk about. Here is in fact that the cybergang RansomHouse, after the ransom monetization with the union of the Valdisieve and Valdarno municipalities went unsuccessful, publishes after about 2 weeks the data within its data leak site (DLS). Read more about it : here

KNAB comes under cyber attack; political parties financing database and mobile apps down
Due to a recent cyber attack the databases managed by Latvia’s Corruption Prevention and Combating Bureau (KNAB), including Electronic Data Entry Systems, and the institution’s official mobile app Ziņo KNAB have been disrupted, as confirmed by KNAB. KNAB reports that in the evening on 25 July multiple of the institution’s resources suffered a cyber attack. Public accessibility to those resources was disrupted by those cyber attacks. Read more about it: here

Lockbit claims to have released data allegedly stolen from LaPosteMobile
The ransomware group Lockbit claims to have released data allegedly stolen from LaPosteMobile. The data appears to include a database containing customer information including names, email and physical addresses, phone numbers, bank details and dates of birth. It is understood that negotiations with LockBit 3.0 have not yielded any results in the past month, resulting in the release of the data. Read more about it : here
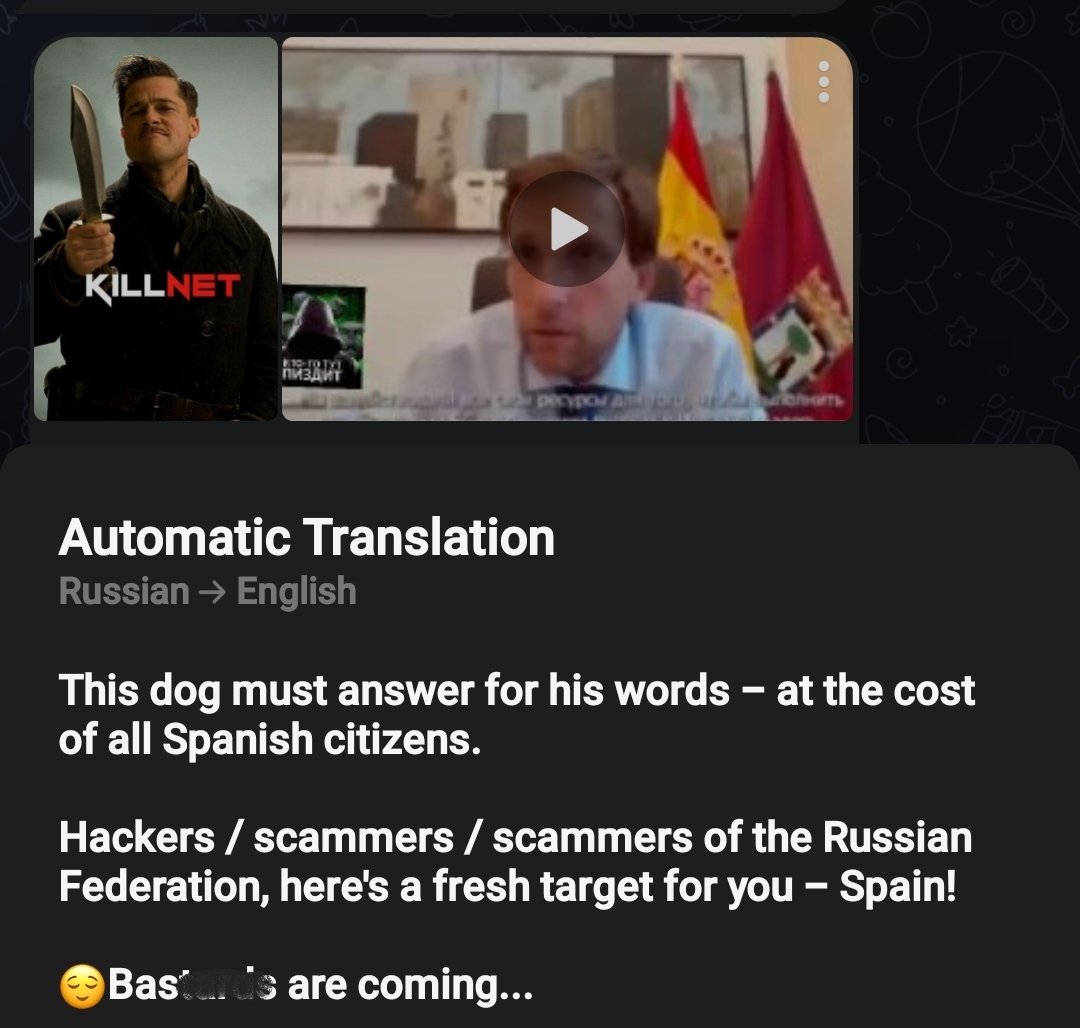
“From Russia With Love” group targeting Ukrainian governement
From Russia With Love. Frwl claims a successful use of Somnia ransomware on Ukraine governmental system. No financial motivation, only destruction. If confirmed its a capability uplift they have planned for months. Read more about it : here
Spanish police arrest two accused of hacking radioactivity alert system
Spain’s National Police said Wednesday that two people have been arrested for allegedly hacking the country’s Radioactivity Alert Network (RAR) and disabling more than one-third of the sensors that are used to monitor excessive radiation levels across the country. The attack occurred between March and June of 2021, and was allegedly carried out by two individuals who were at one point involved in maintaining the system, which is run by Spain’s General Directorate of Civil Protection and Emergencies (DGPCE). The police did not disclose the names of the arrested individuals, or say what motivated the attack. “During the investigation it was determined that the two detainees had been responsible for the maintenance program of the RAR system, through a company contracted by the DGPCE, for which they had a deep knowledge of it that made it easier for them to carry out the attacks and helped them in their efforts to mask their authorship, significantly increasing the difficulty of the investigation,” the National Police said. Read more about it: here

LockBit 3.0 Ransomware Victim : FAAC Group
According to the Redpacketsecurity media, the cybercriminal ransomware as a service group LockBit 3.0 has claimed responsibility for an attack on the Italian-based international group "FAAC" and published this claim on 13 August 2022. Read more about it : here

The german gymnasium of Gunzenhausen affected by cyber attack
For a time, the IT system of a Franconian grammar school was completely paralysed. The reason for this is said to have been a cyber attack. But who is behind the attack? The IT systems of the Simon-Marius-Gymnasium in Gunzenhausen were temporarily unavailable last week. The reason was a cyberattack. The district administration Weißenburg-Gunzenhausen informed about this in a press release on Tuesday (09.08.2022). Now the search for those responsible begins. According to the district office, unauthorised access to the school's network was detected last week. This caused the deletion of data on the school server. The incident was promptly detected and all necessary measures were taken. However, it is still unclear whether the perpetrators were able to steal sensitive data. Read more about it : here

KillNet claims DDoS attacks against “Energijos Skirstymo Operatorius” (ESO) and “IGNIS” Lithuanian energy companies
#KILLNET claims to have launched #DoS attacks against Energijos Skirstymo Operatorius AB (#ESO), an energy company based in Lithuania 🇱🇹. ESO's website appears down at the moment... Read more about it: here Lithuania's state-owned energy group Ignitis said it was hit by "the biggest cyber attack in a decade" on Saturday. Ignitis said it had experienced DDoS attacks, affecting the operation of its websites and digital services. However, the attacks were taken under control by noon the same day. "There were no recorded hacks into the systems or other adverse effects," the group said in a statement. Ignitis later resumed digital services for customers, but the cyber attack on the infrastructure continued. . Read more about it: here