Ciberseguridad en #espacio: cómo se está enfrentando Thales a los desafíos que están por llegar
Europe News
Cyberattack Disrupts Trains in Denmark
On 05 November 2022, all trains operated by DSB, the country's largest rail operating company, were stopped for several hours. According to a DSB press release, the security incident originated at Supeo, another Danish company that provides various services to railway companies and other public and private transport organisations. The attack was therefore not directly directed against DSB but probably against this service provider. Indeed, Supeo provides DSB with a train driver application to access essential operational information when operating railway lines. The service provider suddenly decided to shut down its servers following the security incident, blocking the services they provide and forcing the drivers to stop. The nature of the cyber attack has not yet been communicated by Supeo, which is probably awaiting the conclusions of the cyber research teams. Supeo's response methodology suggests that they were trying to prevent malware from spreading across their various working platforms. This is a classic reaction to a ransomware attack to freeze the situation and prevent it from escalating. It is possible that a claim of attack will soon appear on one of the leak sites of a ransomware group. Read more about it : here

Seine Maritime Department targeted by a cyber attack
On Monday 10 October 2022, the management of the French department of Seine Maritime issued a press release announcing that its networks would be cut off and that its services would be severely degraded. An investigation was opened by the cybercrime prosecutor's office for cyberattacks. Although no ransom demand has been communicated for the moment, the modus operandi of the attack strongly suggests ransomware. While it will still be possible to deal with the department by telephone and on paper, many online services, particularly for disabled people, will remain offline for an indefinite period, which will have a significant impact on many citizens of Seine-Maritime. Read more about it : here

Moscow university was hit with a cyberattack allegedly by Ukraine
Hacktivists or the Ukrainian state, with possible support from "Langley" (CIA), cyber-attacked Moscow University during a master's degree in hybrid warfare. The university's security teams claimed that it was apparent that part of the attack originated in Washington and part in Kiev. According to these claims, some US authorities wanted to disrupt the university's hybrid warfare programme. Read more about it : here
Avos Locker claims the ransomware attack on Casa
According to Valery Marchive, managing editor of "MAG-IT", an attack on the Belgian-based Casa Shop on August 8 was claimed by the cybercriminal group AvosLocker. The amount of the ransom or the nature of the data has not been communicated, however it seems that no customer data has been stolen. Read more about it : here

Phishing campaign targeting Poland
A phishing campaign is currently targeting Poland, with attackers posing as "binzes.gov.pl.", a public service for entrepreneurs. The email typically contains: "The notification will be available on your authorised account until 09-17-2022 and if you do not read it within the specified period, appropriate consequences will be triggered (...)". A copy of the notification mentioned in the fake email is included in the email attachment but it is a fake document which is actually a malicious web script. When it is opened, the computer is infected. Read more about it : here

IT Army of Ukraine has target Gazprombank
On the morning of 6 September, the pro-Ukraine hacktivist group "IT Army of Ukraine" claimed to have attacked the website of the bank "Gazprombank". The bank, wholly owned by Gazprom, is the third largest bank in Russia in terms of assets and investments. The website was still inaccessible on 6 September at 4pm. Read more about it : here

Eni company under cyber attack, perhaps from Russia
Eni, too, after Gse, reports that it was attacked on the IT level. But with minor damage, unlike Gse, which is still down. Various experts suspect an attack from Russia, at a time when energy plays a critical geopolitical role Read more about it : here

Swedish Election Authority hit by three cyber attacks on day of vote
According to officials at the Swedish website val.se, the site faced serious technical problems as a result of DDoS cyber attacks from 10 to 11 September. The head of the authority's secretariat said on 11 September: "There have been three DDoS attacks against val.se, one yesterday and two today. The most recent one is still ongoing. During the elections, the Swedish regional governments also reportedly experienced problems with their telecommunication facilities, but this did not disrupt the elections or their outcome. Read more about it : here
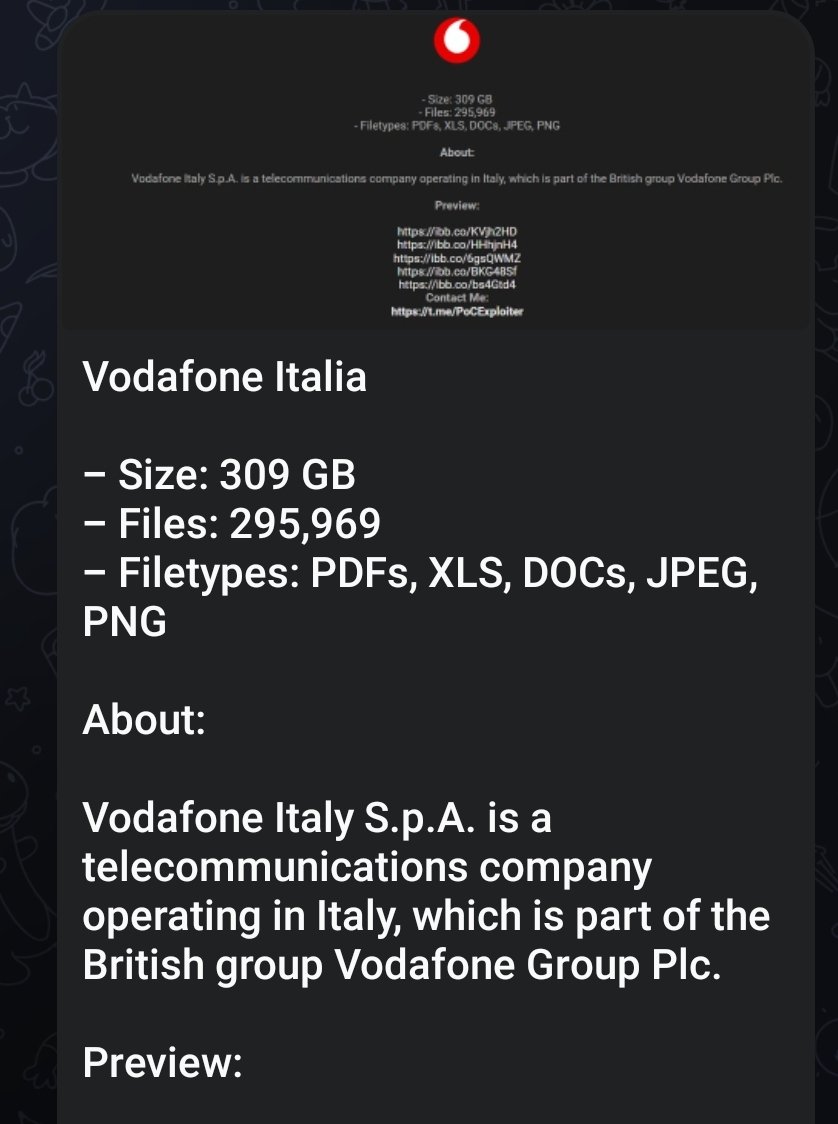
Vodafone Italy under cyber attack
According to the cyber media, the cyber actor PoCExploiter has announced that the telecommunications operator Vodafone Italy has had approximately 309 gigabytes of data stolen. This data may already be exposed on the net, although no information is available at the moment to confirm this. Read more about it : here

LockBit 3.0 Ransomware claim attack on artdis.fr
On 14 September 2022, LockBit 3.0 claimed responsibility for a ransomware attack on the French online company artdis.fr. The company specialises in express delivery throughout France and Europe, storage, order picking and redistribution. The data will be released on 29 September if the ransom is not paid. No information on the nature of the data has yet been provided. Read more about it : here