Bringing cybersecurity globally to critical and complex key activities
Understanding the cyber threat:
Civil society refers to non-profit, citizen-based groups that are organized at the local, national or international level. These groups can take a variety of forms, ranging from unions and communities to think tanks and NGOs. The very nature of their activities (often related to the political sphere) coupled with limited budgets (non-profit) to implement protective security measures make them an enticing target for malicious actors. This intuition is borne out in the wild as civil society organizations and faces a dense cyber threat landscape, both in terms of numbers and variety of threat actors. From a hacker’s perspective, the Civil Society represents a rich environment as organizations process credit card data for donations and may store personal information or even IP data.
NGOs appear in many aspects as the embodiment of the challenges faced by the Civil Society as a whole. According to a survey conducted by the Institute for Critical Infrastructures over NGOs and NPOs, 50% of the respondents revealed they had been targeted by a ransomware and nearly half (49%) admitted they did not rely on a specific unit to deal with cybersecurity issues. This gap can be explained in part by the participatory funding of these organizations and the prioritization of expenditures towards operational needs.
Looking at charities, which are critical in the civil society ecosystem, a few trends are worth noting. First, while many services have gone digital, the rate of reporting cyberattacks has remained steady. Just over one in four charities (26%) reported being the target of a cyberattack in 2020, and this trend seems to correlate with the size of the organization, as 68% of very high revenue charities recorded at least one cyber incident. 80% of breaches involve a phishing scheme.
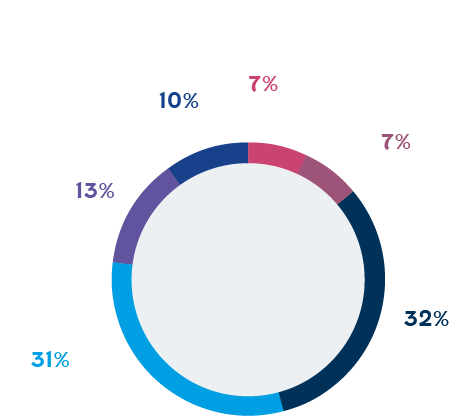
At 32%, NGOs represent the largest sector targeted by nation-state nefarious activities, ahead of professional services and government organizations at only 13%. While both government agencies and politically oriented NGOs collect public policy information, the lack of safeguards encourages threat actors to prioritize targeting the latter civil society organizations. In 2019, Microsoft observed 740 intrusion attempts from nation-state actors targeting democracy-focused civil society organizations in the U.S.-including political parties and think tanks involved in the election process. The structure of American civil society is interesting because organizations in this ecosystem are hailed as major players in the national political debate. This has prompted adversaries of the United States - namely China, Iran and Russia - to launch cyber operations to retrieve any sensitive political content that these organizations may have. This includes projections on the leading policy issues as well as staff and contact information.
Chinese-affiliated actors have launched particularly aggressive campaigns targeting U.S.-based NGOs working on issues related to human rights and democracy in China. In these campaigns, the exfiltration of sensitive data has not been limited to the NGO’s programming but has included a wide range of internal information, including legal and research resources. This gave them a very clear picture of how these civil society groups operate.
![]()
• Spear-phishing: use of spoofed email address to send malicious URLS and ultimately gain credential access of employees
• CEO fraud: combines spear-phishing and identity theft to lure naïve employees into making money transfer. The associations Save the Children and Roots for Peace both lost more than $1 million following a CEO fraud
![]()
It is undeniable that political campaigns represent an opportunity for attackers seeking to undermine trust in the electoral process. As such, democracy-based organizations face intensive malicious activity as election periods approach. The 2016 U.S. and 2017 French presidential elections were marked by numerous cyberattacks, which attempted to undermine Western democracies. In 2016, two groups of Russian hackers successfully penetrated the U.S. Democratic National Committee network and exfiltrated sensitive emails in an effort to support Donald Trump’s candidacy.
- 2014: a report by FireEye revealed APT28’s activities and its specific targeting of civil society particularly journalists - to monitor public opinion and political dissent. This pattern was echoed by TrendMicro, which identified civil society as the primary target of APT28’s domestic operations
- October 2018: Citizen Lab released a report revealing that the Saudi Arabian government had infected with a spyware the phone of the political dissident Omar Abdulaziz. The spyware was identified as “Pegasus”, a product developed by Israeli company NSO group
- • May 2021: High-profile targets within the Uyghur community in China and Pakistan were targeted by a phishing campaign in which Chinese hackers posed as the United Nations to trick users into opening a link that would install a backdoor. The objective of this campaign was cyber-espionage Interestingly, cyber attacks against civil society receive little attention from leading CTI firms. This may be due to the lack of financial resources for civil society to purchase threat intelligence. Therefore, one should keep in mind that commercial threat reporting will tend to focus on sectors that can afford CTI services rather than segments that cannot