Bringing cybersecurity globally to critical and complex key activities
Network traffic encryption
Datacryptor® Model 5 Portfolio: protecting your most sensitive data
In the face of constantly evolving attacks on sensitive data and operational activities, it is increasingly necessary for organisations to secure and protect their critical data and functions. Moreover, the critical importance for certain organisations to retain freedom of action and sovereign control over crypt-key capabilities requires them to have independent development and implementation of algorithms.
Based on over 40 years of experience, the Thales Datacryptor® Model 5 (DCM5) Portfolio provides a suite of high-assurance, high integrity, tamper-resistant capabilities – for network traffic encryption, remote management, code signing, key management, certificate management, and more.
An adaptable, secure and sovereign capability
DCM5’s unique flexibility, ease of deployment and field upgradeability allows customers to assemble affordable, manageable and secure environments based on their required capabilities and levels of trust, while retaining full sovereign control.
Modular components can be assembled to effectively meet the demands of different use cases, and to seamlessly integrate into customer systems, all within a common management ecosystem. Some common solutions are readily available as off-the-shelf products from Thales. Others can be created by Thales or by third party developers, system integrators or customers. As an example, the Datacryptor® Model 5 IP Encryptor product range is
assembled as follows:
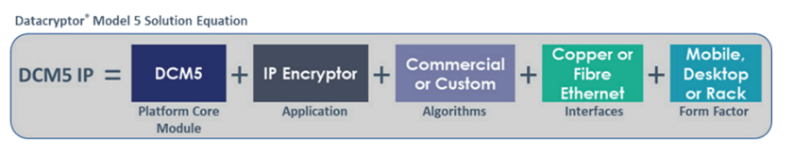
The Datacryptor® Model 5 IP Encryptor product range
At the heart of the portfolio is a small industrial-scale Platform Core Module – a high integrity hosting platform providing core cryptographic and security capabilities to securely boot, update and assure the runtime operation of applications. It can host different applications as required (e.g. IP Encryptor, HSM, various Link Encryption protocols, or other Crypt Key or critical functions). Third party developers and customers have the ability to develop and deploy custom applications and algorithms, providing a high degree of flexibility and customisation. For sovereign solutions, customers can take full control of products, applications, algorithms and roots of trust.

Match your security needs
The Thales DCM5 portfolio establishes a common crypt key ecosystem across your enterprise and provides the flexibility to match your security needs:
• Simple Integration – tailorable form, fit and function of solutions.
• Licence free, send anywhere – Designed to minimise import/export restrictions for unencumbered use.
• Customisation and sovereignty – Applications and algorithms can be customised either by Thales, third party partners or customers themselves, enabling new capabilities to be developed without reliance on Thales. Customers can choose to take full sovereign control of customised units.
• Updateability – with different applications or algorithms to re-role deployed units and to support changing requirements, including Quantum Resistance. New or updated algorithms and applications can be developed by Thales, Customers or Third Party partners.
• Reduced operational complexity – remote configuration and lifecycle management of deployed units (including commissioning and re-keying) reduces cost of ownership and allows equipment roles to be changed during deployment.
• Consistent Management – Common management approaches across the portfolio.

Ease integration
• Reduced spares holding – Spares can be held unkeyed and unloaded at remote sites, without customisations that might increase security classification. Common spares can be configured to replace units of a particular function only when required. Minimal handling restrictions (e.g. Official ACCSEC) may apply when firmware is loaded. By reducing spares holdings and handling requirements, shipping and holding DCM5 spares is simpler and more cost effective than for other cryptographic devices.
• Simple keying – Units can ‘self-key’ over the network under the secure remote control of Network Managers, with reduced reliance on external authorities and cumbersome delivery mechanisms.
• Assurance – Designed and built to the UK High Grade Engineering Standard provide assurance for the most critical use cases, where data must be protected against sophisticated, well-resourced and determined threat actors:
· Provable Security, Safety and Timing Criticality.
· Suitable for enterprise, operational and industrial environments.
· Provably defensive against highly targeted Cyber Attacks.
· Robust supply chain and manufacturing assurance.
• Rapid Development, Evaluation and Deployment – modular approach built around a common Platform Core Module.
• Designed and manufactured in the UK, based on over 40 years of experience.