HarfangLab EDR: Driving Cybersecurity Proficiency
In a rapidly evolving digital landscape, safeguarding corporate servers and endpoints against cyberattacks is paramount. In our interconnected digital age, where employees rely on multiple devices for work, the complexity of threats has escalated. Organisations face an ever-evolving adversary landscape, with cybercriminals constantly devising new ways to exploit vulnerabilities. Endpoint Detection & Response (EDR) emerges as a critical defense mechanism.
What is EDR?
Endpoint Detection & Response is a cybersecurity solution that monitors all endpoints within an organisation’s network. These endpoints include laptops, desktops and servers. EDR tracks various activities on these endpoints, such as user behavior, system logs, and network traffic. When it detects suspicious behavior or potential threats, it alerts the teams and takes necessary actions to prevent breaches.
HarfangLab EDR is a Next-Gen solution designed for cyber experts. It focuses on practical results rather than buzzwords. We will see examples of this solution in the article.
Who is HarfangLab?
HarfangLab, founded in 2018 and headquartered in Paris, France, is a trailblazer in the field of cybersecurity. Led by former professionals from the French Cybersecurity Agency (ANSSI), HarfangLab brings expertise, innovation, and resilience to the forefront of endpoint protection. HarfangLab is a key partner of Thales Cyber Solutions Belgium. Let's find out what HarfangLab can bring to the security of your organization.
HarfangLab EDR: The Advantages
Endpoint Detection and Response (EDR) systems are part of modern cybersecurity strategies, tasked with safeguarding endpoints like workstations and servers, from a wide array of threats. These systems work by continuously monitoring and collecting telemetry data, including process activities, network connections, and file changes. This data is then analyzed in real-time, allowing for the swift detection of potential security incidents and enabling rapid response measures to contain and mitigate threats before they can inflict serious harm.
An important factor that makes Harfanglab stand out is the ability to customize detection rules. While all EDR systems come with preset rules to identify most common threats, these may not be enough in some use cases that require a specific customization, as we will see later in this blogpost.
HarfangLab's EDR solution allows users to create their own detection rules using open format like YARA or SIGMA.
Sigma & Yara rules Overview
Sigma
Sigma is an open standard that enables the creation and sharing of rules designed to detect malicious or dangerous behaviors on information systems.
It is a vendor-agnostic standard, so Sigma detection rules can be shared across various security products (Splunk, Sentinel, etc...).
Sigma rules are written in YAML.
To better understand how it works, let's have a look at this example rule that detects when an exclusion has been added to the Windows Defender Antivirus.
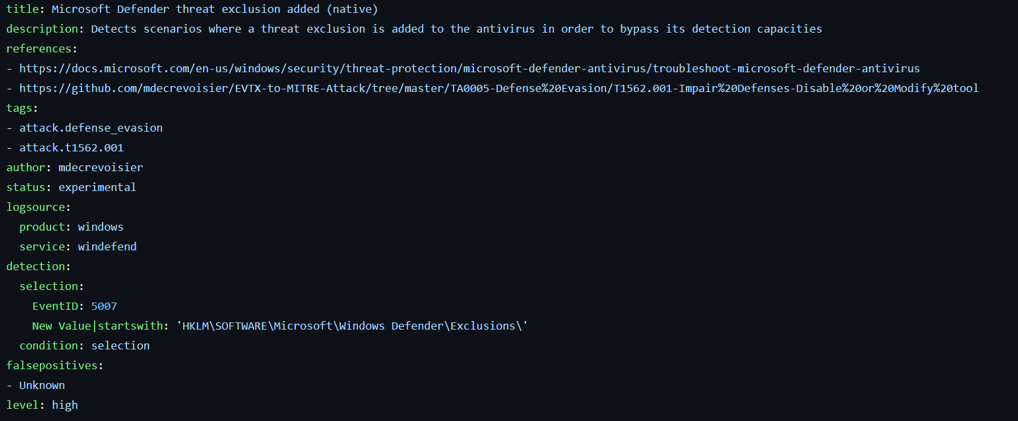
A Sigma rule is separated into three components:
- Metadata
It contains metadata information such as the title, description, author, etc. - Logsource
The type of event/logs we are looking into. - Detection
The rule content.
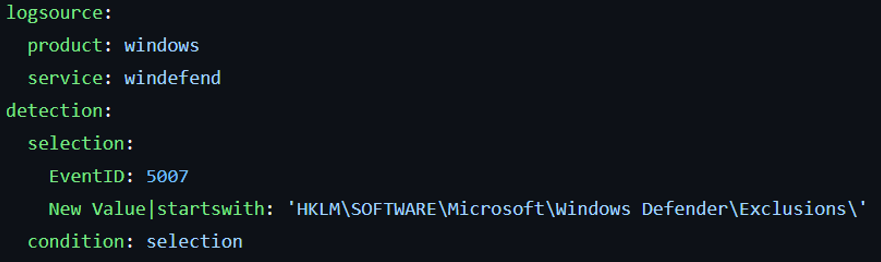
All the detection logic happens in this section, while the other fields are related to metadata.
Let's have a breakdown of the components:
Logsource
The logsource section defines where the rule will look for data. In this case, it specifies:
- product: windows - This indicates that the rule is applicable to Windows operating systems.
- service: windefend - This specifies that the rule is monitoring the Windows Defender service.
Detection
The detection section contains the logic that identifies suspicious activity. Here’s an overview of its components:
Selection: This is where the specific conditions for detection are defined.
In this case, the rule is looking for:
- EventID: 5007: This Event ID corresponds to events where settings in Windows Defender have been modified.
- New Value|startswith: 'HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\': This condition checks if the new value starts with the specified registry path, indicating that an exclusion has been added to Windows Defender.
Condition: Selection: This line indicates that the rule will trigger an alert when the conditions specified in the selection are met.
As you can see, Sigma rules are more targeted at identifying malicious behavior.
Yara
Yara is a tool aimed at detecting malware using pattern recognition.
In contrast to Sigma, which focuses on behavioral detection, YARA aims to identify textual or binary patterns in a file that are known to be associated with a malware.
This is far more efficient than using hash signature recognition as the hash can easily be altered.
Let's look at this example:
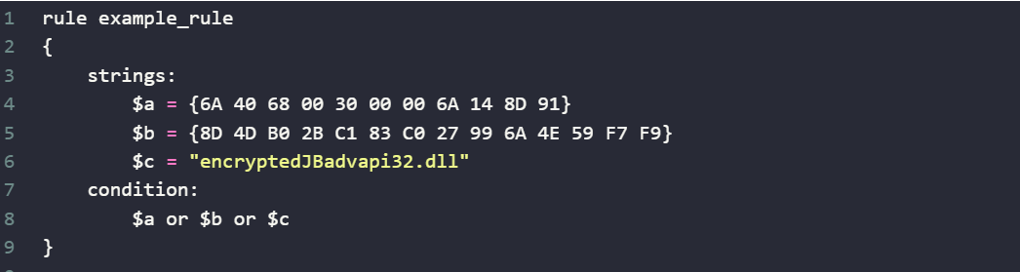
Strings Section:
In the strings section, we define the specific patterns that the rule will search for in files or memory. These patterns can be hexadecimal byte sequences or plain text strings. In this rule, we have three patterns:
$a = {6A 40 68 00 30 00 00 6A 14 8D 91}
$b = {8D 4D B0 2B C1 83 C0 27 99 6A 4E 59 F7 F9}
$c = "encryptedJBadvapi32.dll"
The condition section defines the logic for when the rule should trigger a match. In this case, the condition is:
$a or $b or $c
This means that if any one of the patterns $a, $b, or $c is found, the rule will be satisfied.
A Case Study: Ransomware operators targeting Atera agent
Nowadays, businesses rely heavily on Remote Monitoring and Management (RMM) tools to keep their IT infrastructure running smoothly. Several options are available on the market: TeamViewer, Atera, NinjaOne, .. These tools provide remote support, remote patching, and monitoring. However, while they help manage IT environments, they can also introduce significant security risks.
Threat actors deploying ransomware have been using these tools to penetrate and move inside the network, exfiltrate data, etc. In contrast with Command and Control tools such as Cobalt Strike, RMM are not usually detected by EDRs. Moreover, some RMM tools are SaaS meaning the attacker does not have to setup its own infrastructure.
What typically happens is that the attackers trick the user into installing the RMM agent, which is preconfigured to be linked with the attacker's tenant. After the installation, the attackers have access to the victim's machine through the RMM web interface.
Another scenario is when the RMM tool is already installed. In this case, attackers might try to reconfigure it to connect to their own tenant. This would allow them to maintain persistence without raising suspicion.
With Atera, this can be done by providing the IntegratorLogin parameter alongside the AccountId.
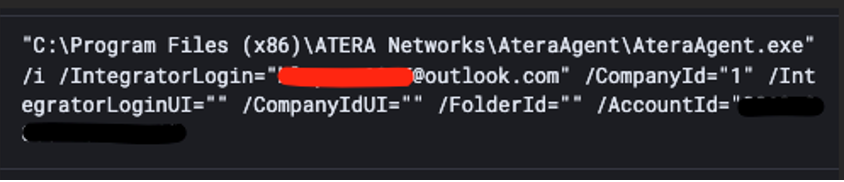
It becomes very handy to protect against this type of attack as Companies cannot simply block the software if they use it for their IT operations. This creates a challenge: how can a company secure the use of Atera without disrupting its operations?
The Solution: Custom Sigma Rules
To address this challenge, let's first examine what happens when the IntegratorLogin parameter is changed through the CLI.
Behind the scenes, the registry key HKLM\SOFTWARE\ATERA Networks\AlphaAgent\IntegratorLogin is modified.

Since Harfanglab collects telemetry data related to registry events, one approach could be to examine the value of this key during a write operation.
This is what the built-in rule from Harfanglab does:
It basically looks for any write event on the registry key HKLM\SOFTWARE\ATERA Networks\AlphaAgent\IntegratorLogin and checks if the value contains one of the following strings:
These are generic email domains commonly used by attackers. While this rule serves as a solid foundation, there's a complication: what if the attacker uses an email service not included in this list?
This is where customization comes into place: instead of having a blocklist of email domains, the rule will establish a list of allowed domain (the ones used by the IT team of the company).
Below is the customized Sigma rule:
This Sigma rule detects if the Atera IntegratorLogin email is changed to something outside of the company’s official domain: bcrp.com.
Let's review the main components of the rule:
- Logsource:
- product: windows - The rule is applied to Windows systems.
- category: registry_event - It monitors registry changes.
- product: windows - The rule is applied to Windows systems.
- Detection Logic:
- EventType: SetValue - The rule looks for events where a registry value is set.
- TargetObject: 'HKLM\SOFTWARE\ATERA Networks\AlphaAgent\IntegratorLogin' - It monitors this specific registry path where the Atera email is stored.
- Condition: The rule triggers an alert if the email address is changed to something that does not end in @bcrp.com.
- EventType: SetValue - The rule looks for events where a registry value is set.
If we now try to change to IntegratorLogin to a non bcrp.com email address, an alert is raised in Harfanglab.
Alternative Attack Vectors
Attackers might exploit other features of RMM tools like Atera beyond just modifying registry settings. They could use stolen credentials to gain access or exploit known vulnerabilities within the tool itself. Custom Sigma rules can be adapted to monitor for these activities as well, such as tracking unusual login patterns, unexpected administrative actions, or attempts to disable security features.
Conclusion
While preset detection rules provide essential baseline protection, the ability to create and adjust rules to meet an organization’s specific needs is what sets this EDR system apart.
Custom Sigma and YARA rules empower security teams to develop targeted detections that address unique vulnerabilities, such as unauthorized changes to registry settings or other critical configurations. The Atera case study demonstrates how custom rules can be effectively used to detect and mitigate sophisticated attacks that exploit legitimate software, offering a tailored solution to real-world challenges.
As threat actors continuously evolve their tactics, you can adapt your detection rules accordingly. This approach enhances your security measures without disrupting critical operations or infrastructure.
In this ever-evolving digital landscape, HarfangLab EDR stands as a beacon of resilience, offering a dynamic and adaptable solution to your cybersecurity needs. This model is not just a tool, but a partner in your journey towards cybersecurity excellence. It’s designed to grow with you, to learn from your unique challenges, and to empower your organisation with the ability to stay one step ahead of threats.
With HarfangLab EDR, you are not just reacting to cyber threats, you’re anticipating them. You’re not just maintaining your defenses, you’re enhancing them.
Reach out to us today for more information on how our services can be tailored to meet your specific needs. Let’s redefine what cybersecurity means for your organization together. Contact us now, and let’s empower your cybersecurity excellence.
Authors
Louis Flamion
Ilyass Mokhtari



