How to Prepare for the NIS2 Directive in Belgium? Discover the key updates and what does it mean for your organisation.
In recent years the digital landscape witnessed the rise of the threats and attacks. In fact, the recent rise of ransomware and phishing attacks is very alarming.
“ …1,435 data breach files, up from1,054 in 2020 (+ 36.15 %)…”
The need for better cyber-security is evident from the Belgian Data Protection Authority’s latest reports; data breaches continued to be a major focus for the DPA in 2021: The DPA opened 1,435 data breach files, up from 1,054 in 2020 (+36.15%). It also opened 35 monitoring files, compared to 30 in 2020 (+16.67%). Almost half of the data breach notifications concerned human errors, and almost a quarter involved phishing, hacking or malware.
This situation necessitates a serious response to these threats. Thus, the EU updates regularly its laws and directives to keep up with the challenging environment, the needs of its citizens and consumers, and so on. To this end many directives and regulations were drafted by the EU commission to support those the member states and group entities: namely the NIS1 / NIS2.
The NIS1 Directive, or the EU “Network and Information Systems” directive, (EU) 2016/1148, was released in 2016 and implemented by 2018. One of its important clauses, NIS Article 23, mandate to be reviewed regularly. In this context as per the amendment mentioned, along with the growing cyber-attacks, digital transformation, pandemic disruption, and remote work, the new directive NIS2, was released on December 2022.
NIS1 & NIS2: How will they impact your organisation?
To assist entities and businesses, protecting themselves in the area of cybersecurity, the EU released the NIS directives as guidelines in this endeavor.
The NIS directives, among others, have been drafted not compliance checklist. Instead companies should view them as standardized tools to help them harmonize the efforts in combating cybersecurity threats across the EU space.
NIS1 Directive only included “operators of essential services” (OESes) and “digital services providers” (DSPs). Currently NIS2, the directive applies to any ‘essential’ or ‘important’ entities, depending on how vital they are for the economy and society.
“…NIS2 covers eight main industry sectors such as postal and courier services, data centers, food, and waste management…”
NIS2 changes and broadens the types of organizations that are covered by the directive. NIS2 covers eight main industry sectors such as postal and courier services, data centers, food, and waste management.
What about other regulations?
For the past decade, EU drafted and published several cybersecurity frameworks and directives to assist companies and government entities to safeguard information and to protect individuals privacy. Some Member states interpreted and twisted the directives according to their benefits and needs due to the lack of enforcement, the EU released a privacy regulation (instead of directives) known as GDPR.
Since GDPR and NIS2 are the latest frameworks, we decided to illustrate their differences and similarities:
GDPR | NIS2 |
Differences | |
|
|
Similarities | |
| |
Why NIS2 Directive?
At the time of NIS1 release, the challenges and the concerns were different than nowadays, the directive assisted organisations and government entities mitigating their risks appropriately. Since the malicious actors tactics, technics and procedures changed with time, NIS1 should be amended. Upon reviewing the NIS1 clauses, the following gaps could be identified:

With such gaps for NIS1, the NIS2 comes to push new aspects that address them, by themes:
Size of companies included in scope
“…NIS2 directive classifies entities into two categories: essential and important …”
The NIS2 directive classifies entities into two categories: essential and important. Both categories must meet the same requirements, but the supervisory measures and penalties differ. Essential entities must meet supervisory requirements from the introduction of NIS2, while important entities will be subject to ex-post supervision. This means that if authorities receive evidence of non-compliance, action will be taken.
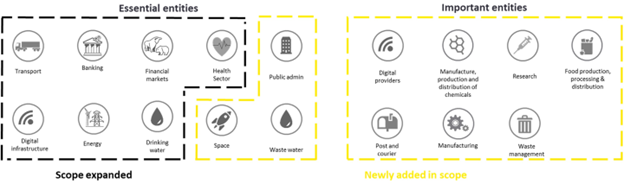
The NIS2 directive has streamlined the scoping process for competent authorities. A range of sectors has been identified, and any large (with a headcount exceeding 250 or revenue over 50 million) or medium (headcount above 50 or revenue more than 10 million) enterprise from these sectors will be automatically incorporated in the scope. However, this does not necessarily exclude small or micro-organizations. If an enterprise meets certain criteria indicating a significant role for society, the economy, or specific sectors or types of service, Member States can expand these requirements.
Registration of crucial and significant entities
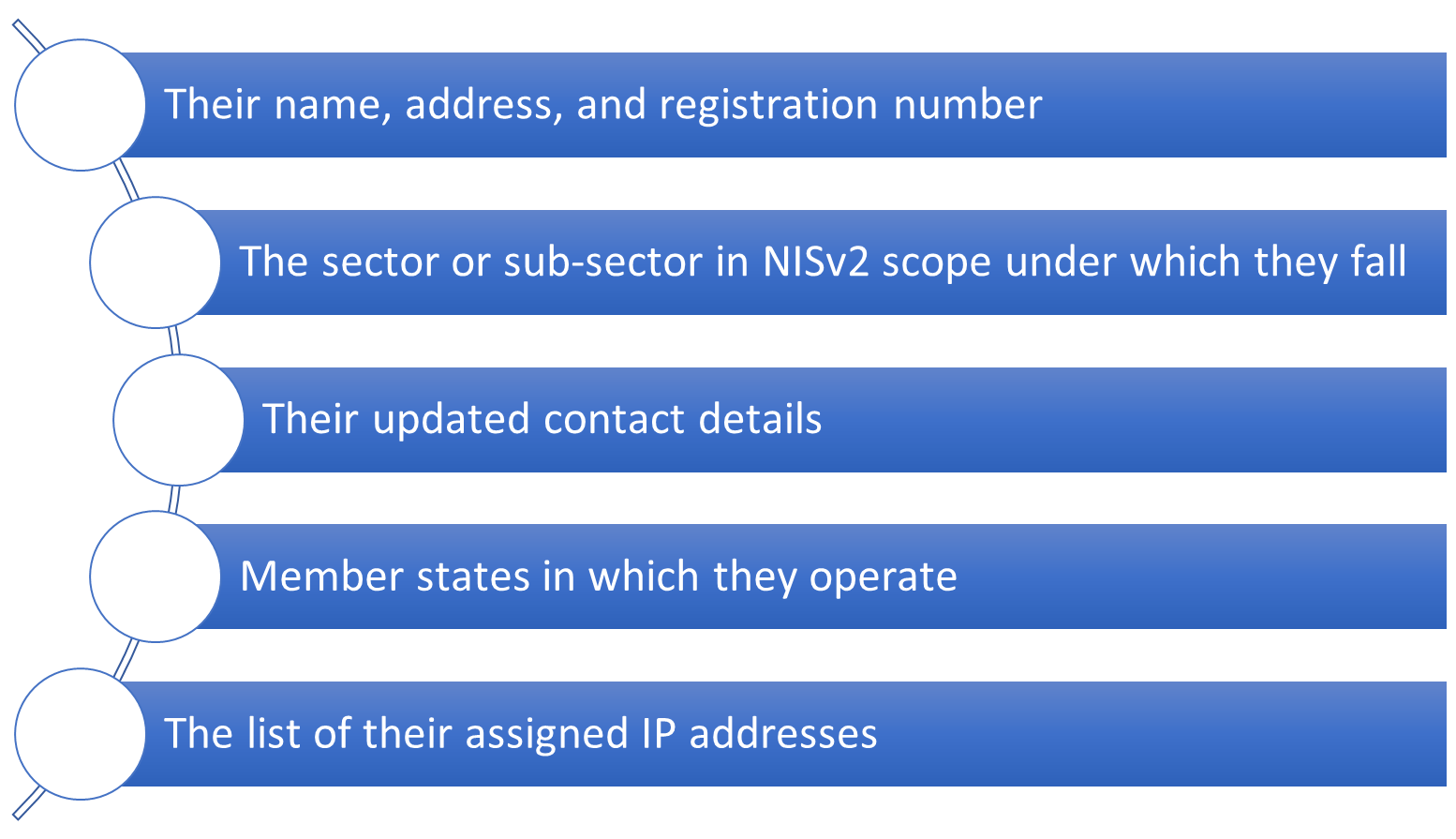
Under NIS2, it is mandatory for Member States to pinpoint the crucial and significant entities within its purview by April 17, 2025. Entities have the option to register themselves, however, they are required to ascertain if their services are encompassed by NIS2, identify the roster of Member States where they offer "in-scope" services, and complete registration prior to the deadline in each Member State.
The registration process will require entities to provide the following information:
Security obligations
The NIS2 Directive pushes new security risk-based obligations. This approach is similar to other regulations like GDPR. How you respond to incidents and manage crises and risks is very important for complying with NIS2 and should guide you in applying the security measures that the directive suggests. Some of the security measures are:
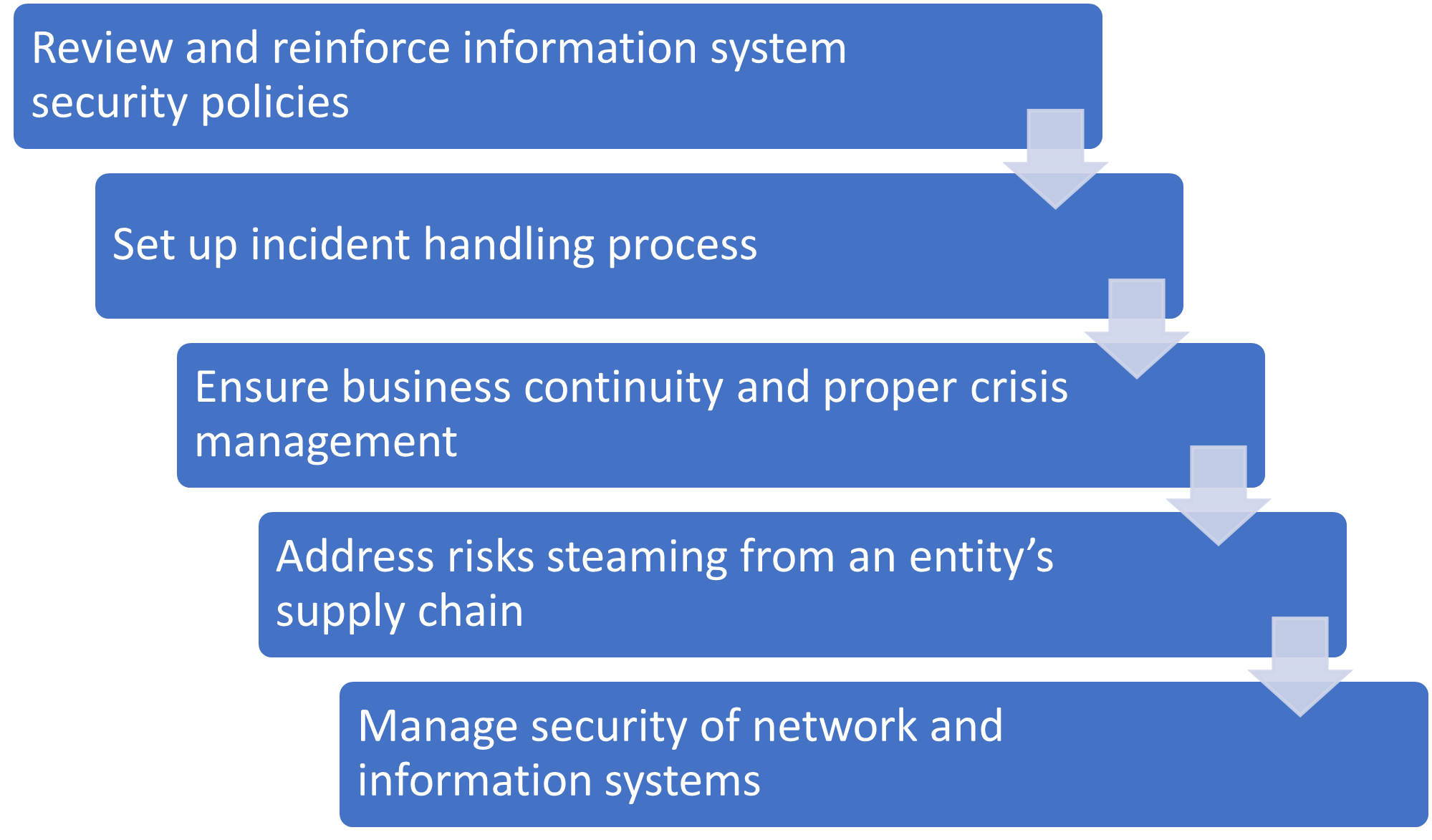
Whether a company is classified as an "important" or "essential" entity under the directive, changes how much they have to do for cybersecurity risk management and reporting obligations under NIS2.
Why Management of third-party risks in the supply chain?
Cyber-attacks often target the supply chain. A 2021 survey from BlueVoyant proved this by interviewing 1,200 CIOs, CISOs , and Chief Procurement Officers about supply chain cybersecurity issues. The results showed that almost all companies (97%) had suffered from a cybersecurity breach that started at a supply chain vendor. NIS2 knows this cybersecurity risk and asks for strict risk management of the supply chain.
Incident reporting
According to the NIS2 Directive, each Member State is required to establish a central contact point for adherence to the Directive, along with a coordinating CSIRT (Computer Security Incident Response Teams) for incident reporting or a suitable authority. In Belgium the CCB (Centre for Cyber Security Belgium) will be responsible for this role.
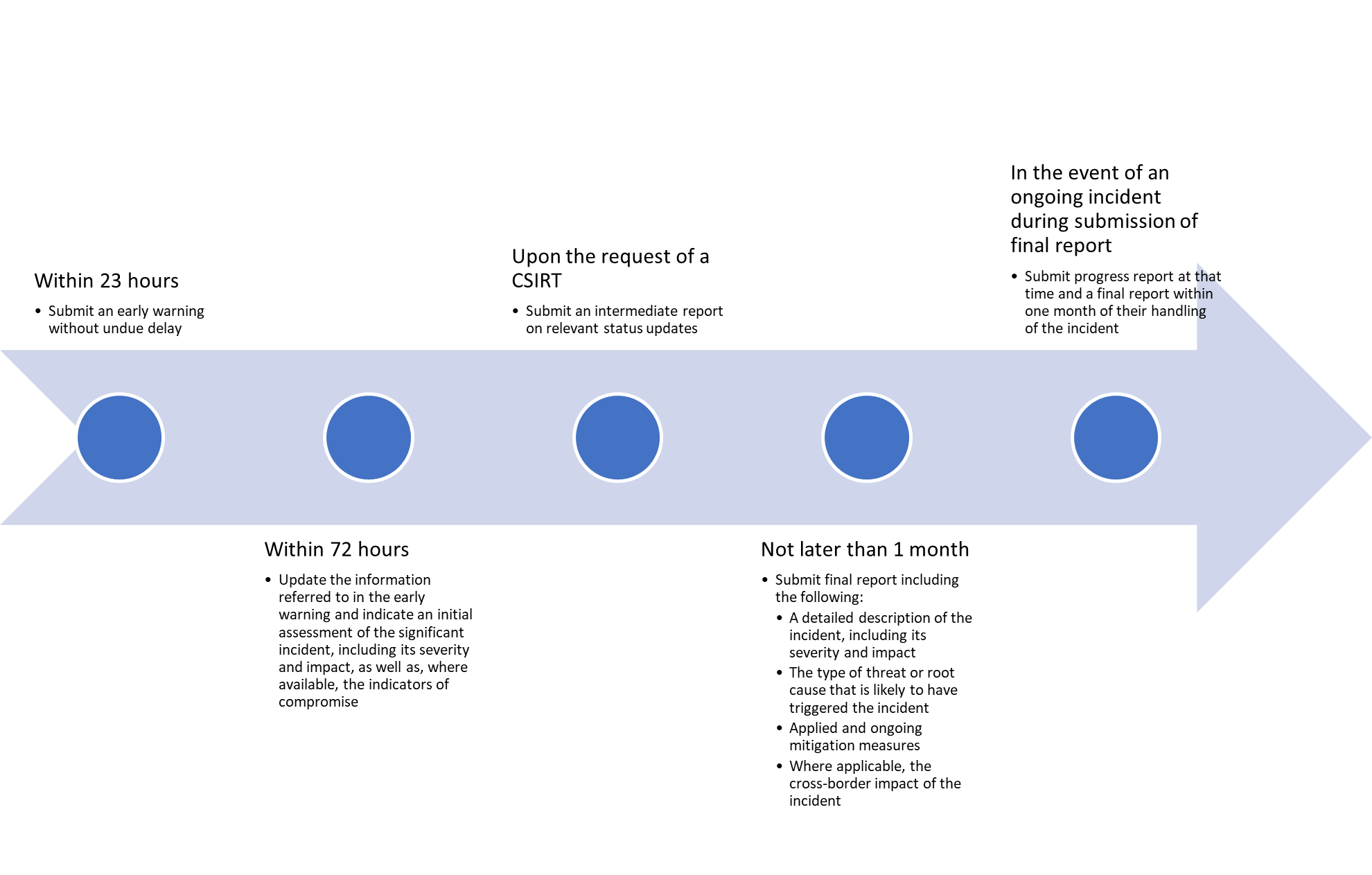
NIS2 has introduced a new timeline for reporting incidents. Essential and important entities must notify any incident with significant impact without undue delay.
An early alert, along with preliminary assumptions about the nature of the incident, should be relayed to the relevant authority or CSIRT within a day. A comprehensive notification report, which includes an evaluation of the incident, its severity, impact, and signs of compromise, must be submitted within three days. A final report must be submitted after a month.
To alleviate administrative load, especially for incidents spanning multiple Member States, the Directive advocates for the simplification of the incident reporting process by establishing a single point of entry for incidents.
Every quarter, the CSIRT, or the relevant authority if applicable, must provide ENISA with anonymized information about the incidents. Using this data, NISA will then produce a report every half-year on the incidents within the EU. This reporting process is vital for organisations and Member States to learn from past incidents and represents a significant shift in the new NIS2 Directive.
Accountability
Company management will be held accountable for compliance with cybersecurity risk-management measures. Risk is no longer the sole responsibility of the IT function, it's the organisation and board as a whole.
Higher fines for non-compliance
Administrative fines of up to 10 million EUR or 2% of the total global annual turnover of the company can be levied for non-compliance with the Directive. In addition to the fines, penalties can include binding instructions to bring security measures in line with NIS2 requirements as well to implement the recommendations of a security audit.
In case of significant cyber threat is likely the entities can be also requested to inform their service recipients of the threat itself.
Least but not last, the NIS2 makes it possible to hold natural persons representing Essential Entities liabl for a breach of their duties to ensure compliance with the Directive.
Wider consequences of the NIS2 Directive for Businesses
Businesses need to determine their categorization under the NI2 Directive, that is, whether they are an essential or significant entity. Occasionally, a business might be in a mixed position, offering both essential and significant services.
The extraterritorial scope impacts any organisation functioning within the EU, meaning a producer with a facility in any specific country will be subject to the NIS2 jurisdiction, even if they manage facilities elsewhere. NIS2 employs language akin to the GDPR when discussing services that fall within the directive's extraterritorial scope. The expanded security responsibilities of the NIS2 Directive will influence all included entities, implying that these firms must gear up for compliance. Any business mandated to adhere to NIS2 should lay the foundation by enhancing its cyber-readiness through a risk-oriented evaluation and execution.
What can you do to get cyber-fit for the NIS2 Directive?
It is important to acknowledge that NIS2 is all about being ready for any cyber problems that might come up. You need to look at the big picture and the worst-case scenarios to protect yourself from attacks. You need to have a good plan to keep your data fit and healthy. But how do you do that?
In cybersecurity, you need to have a smart and practical plan. You also need to think about three things:
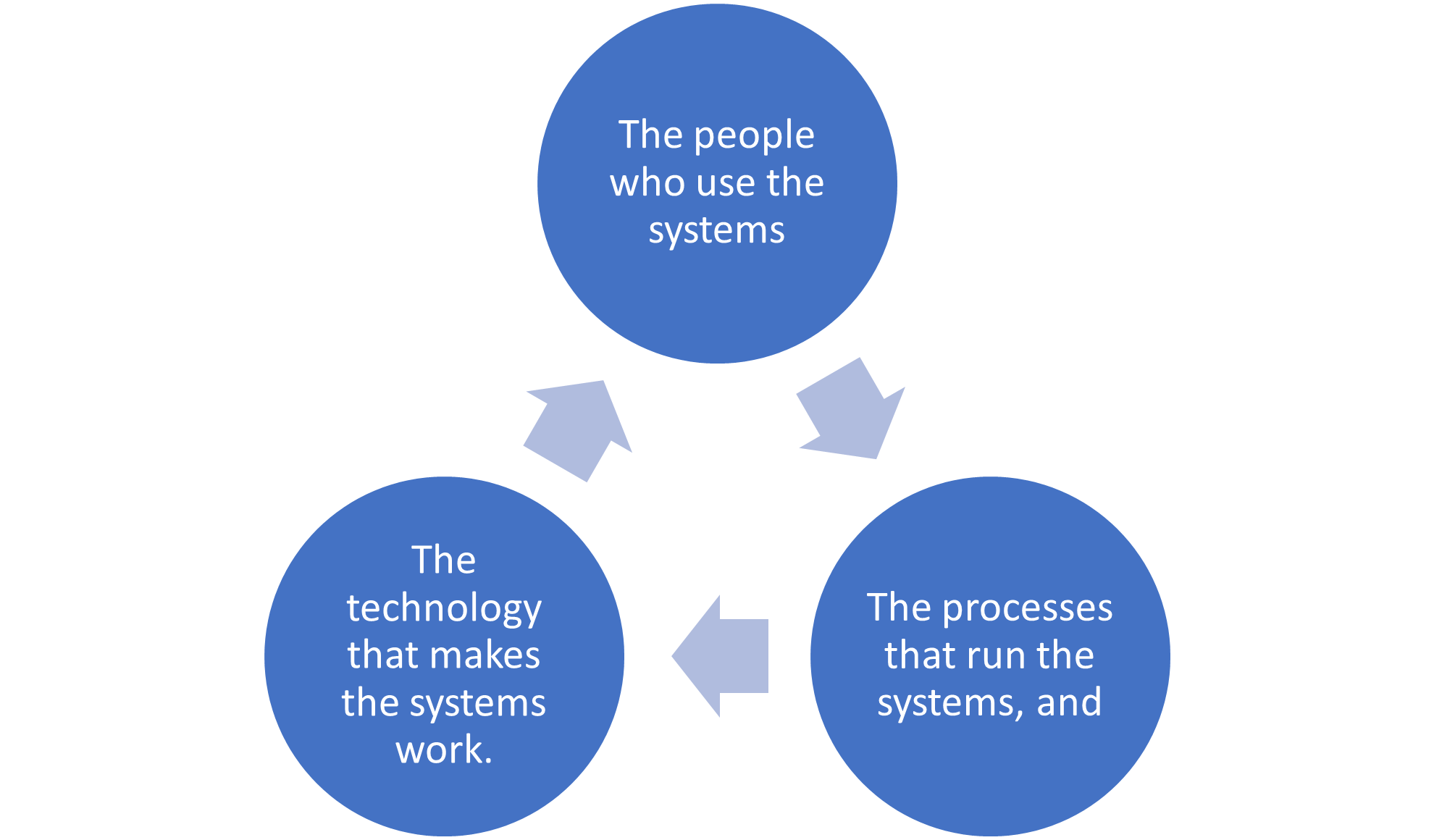
These three things are what hackers and other attackers target to cause trouble. Your work in Cybersecurity is not an easy one, because there are many things that can go wrong, like online services, working from home, or people not following the rules. You need to look at cybersecurity from all angles to deal with these challenges.
A cyber-fitness strategy is a plan to improve your organisation's cybersecurity and resilience against cyber threats. According to some web sources, a cyber-fitness strategy may include the following steps:
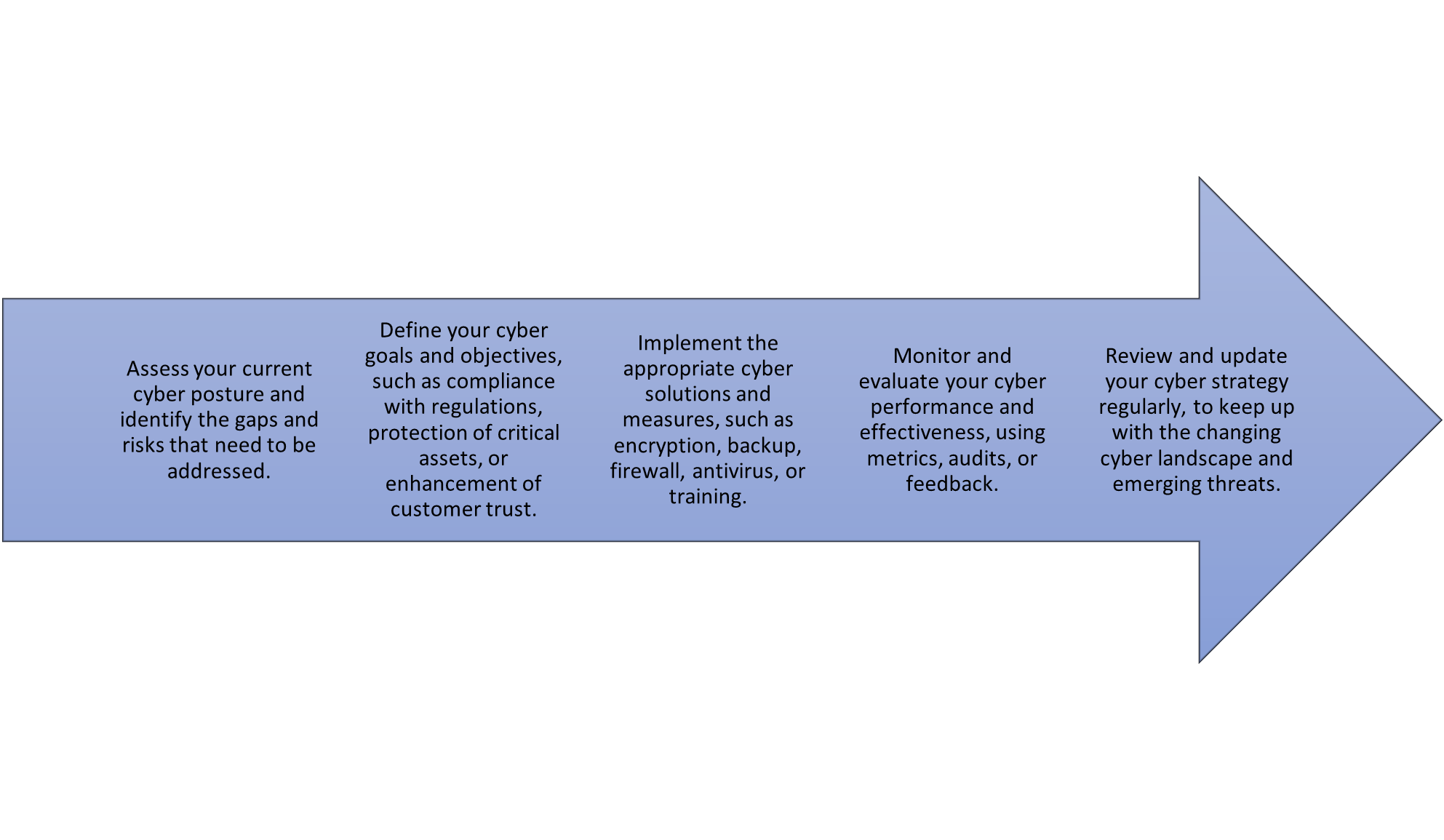
A cyber-fitness strategy can help you achieve a higher level of cyber-resilience and reduce the impact of cyber incidents on your organisation.
A solid cyber strategy encompasses:
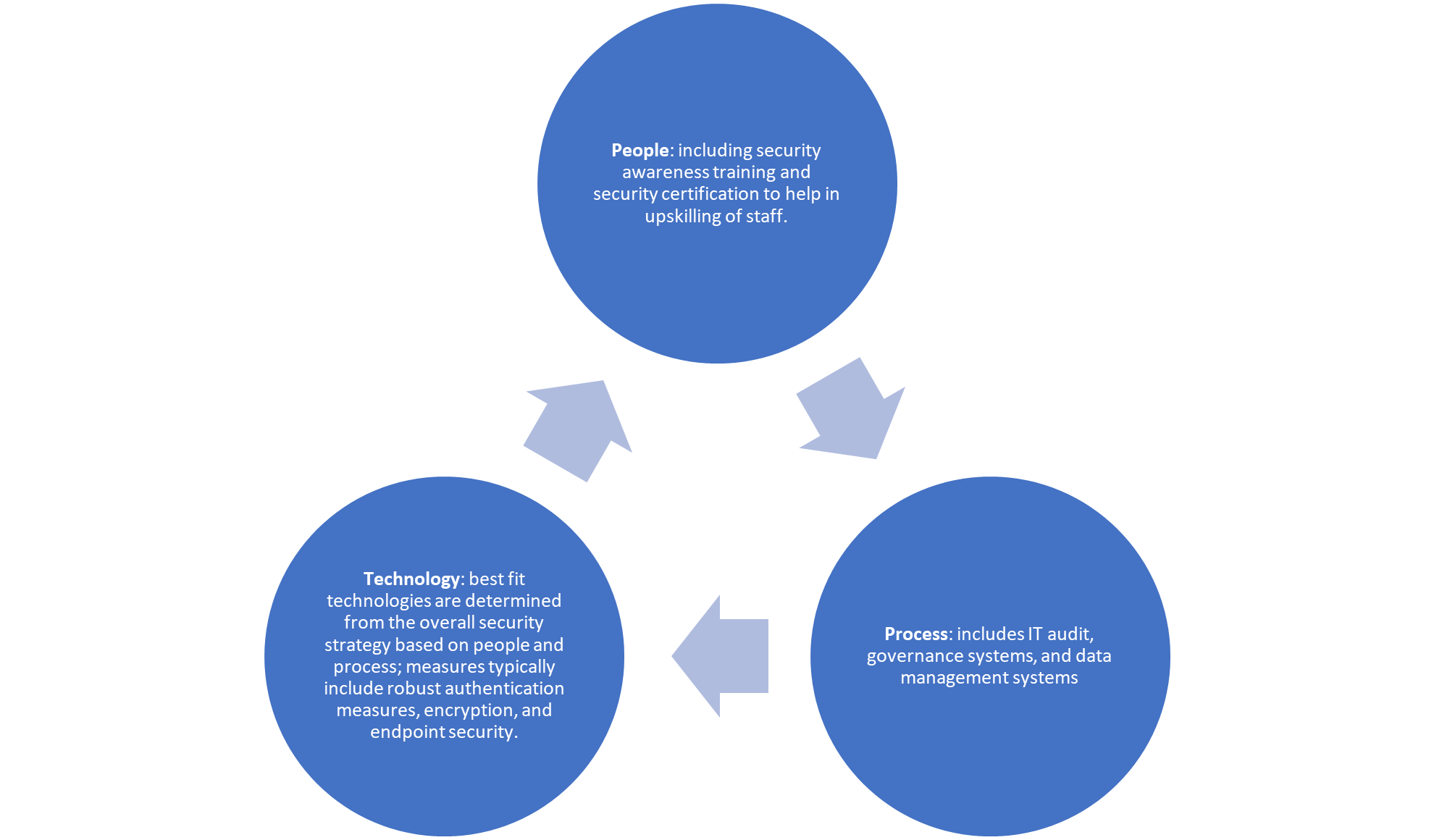
In cyber-security risk mitigation, the whole is greater than the sum of the parts; expert security services use the ethos of people, process, and technology to establish a baseline of cyber fitness for your organisation. The baseline is continually assessed to ensure it meets the needs of changing technology and the cyber-security landscape.
Summing up the steps an organisation needs to follow in implementing NIS2 , here are the important tips that help any company to draw its NIS2 roadmap:
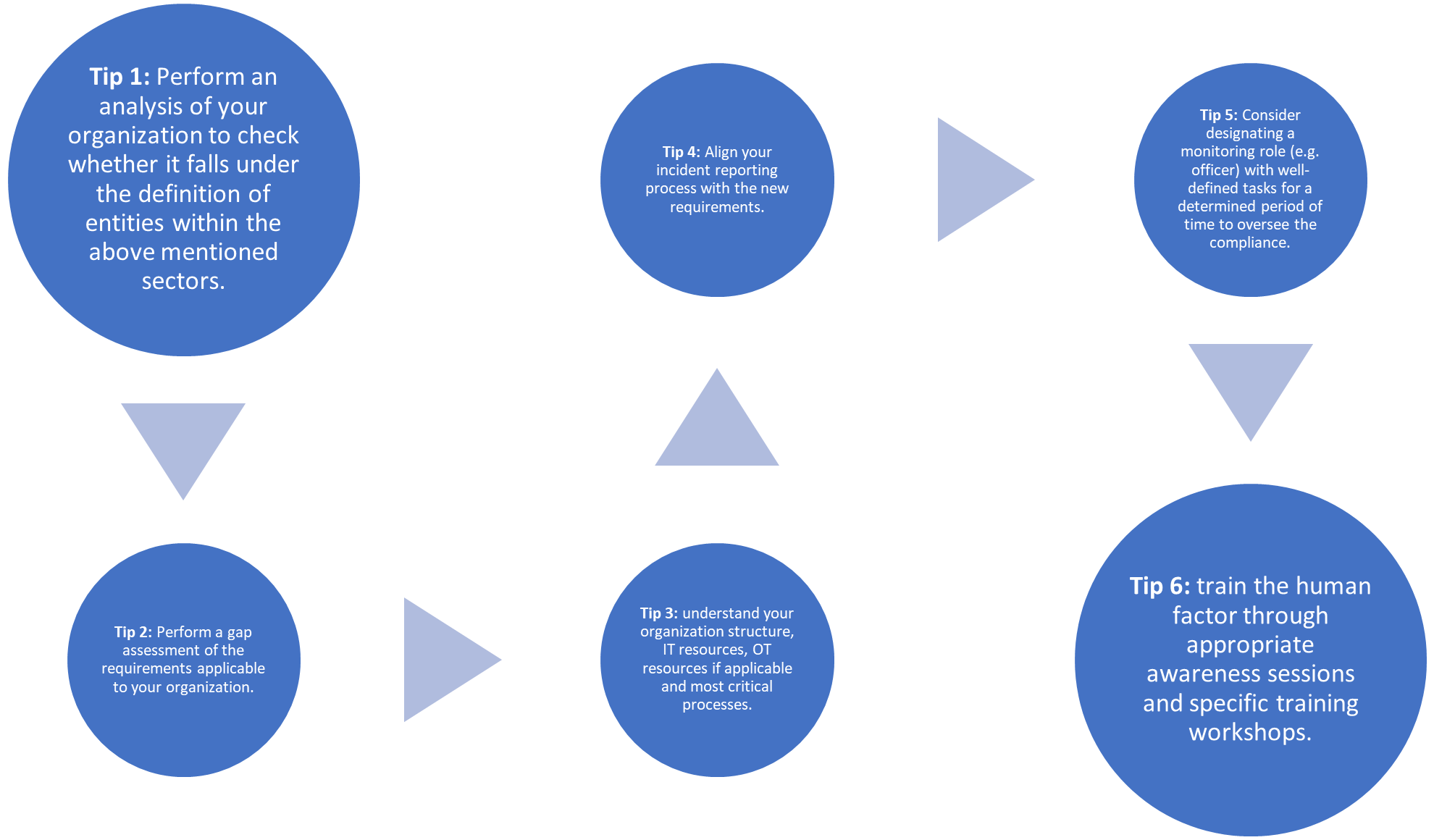
Time for you to get ready!
NIS2 is a good thing for Europe to work together on cybersecurity. But the rules are tough and you need to follow them.
You need to have a good plan that covers your people, your processes, and your technology, so you can be ready for any cyber-attacks and meet the NIS2 standards. If you don't do this, you will have to pay a lot of money.
NIS2 can fine you up to €10 million or 2% of your global sales, whichever is more. That's if you don't manage your risks or report your incidents properly. If you mess up big time, you could face a lot of problems.
You could have to pay for notifying your customers, for breaking the GDPR rules, for the NIS2 fines, and for losing your reputation and your service. That could ruin your business. You have two years to get ready for NIS2, but don't wait too long.
It takes time to get your cybersecurity in shape, so start now to make your company cyber-fit for this important rule. You need a strong cybersecurity strategy to be prepared for NIS2. Thales Cyber Solutions Belgium can help you.
Finding the right partner for your NIS2 journey
Achieving compliance with the NIS2; meaning achieving cyber confidence and resilience to attacks, is critical. Thus, it is important to find the right partner to assist companies in this journey.
Thales Cyber Solutions Belgium comes out as a reliable partner in the NIS2 implementation, we support organisations in all areas of action of the NIS2 journey:

Author
Patrick Aoun, Information Security Governance Consultant
Contact our experts for this NIS2 journey!



