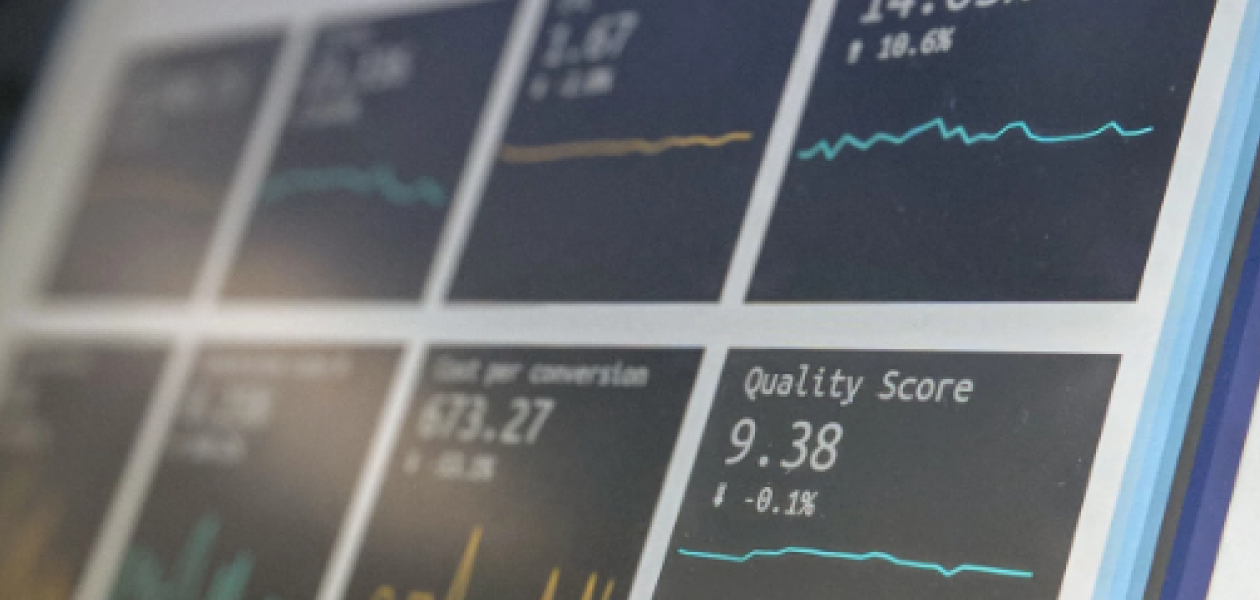
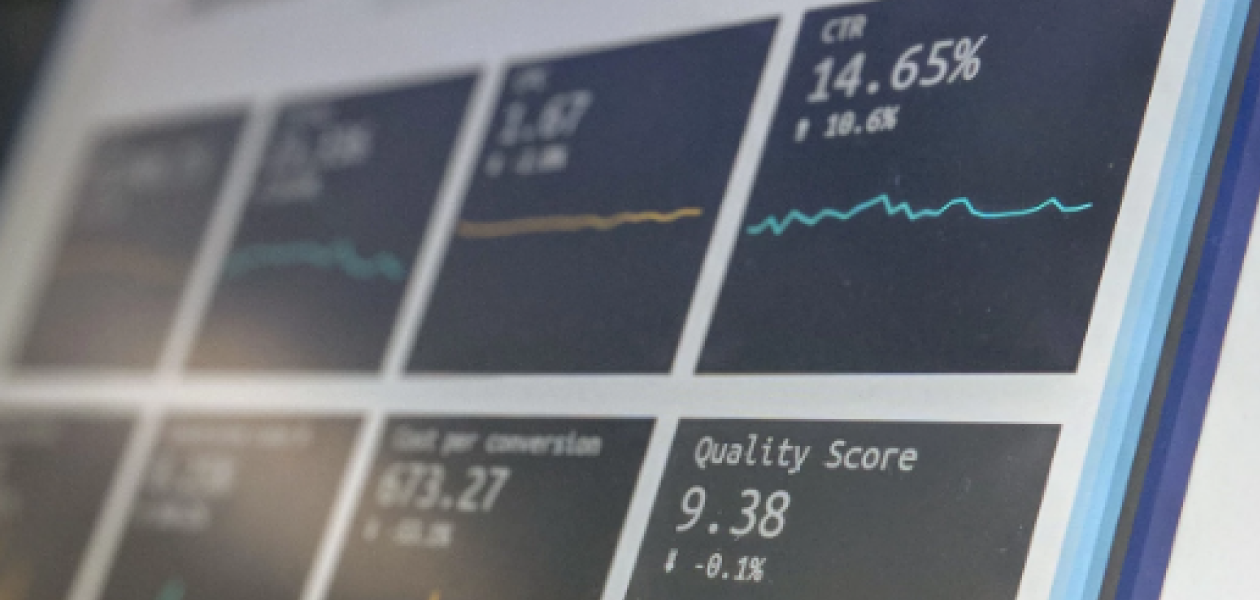
Mobile apps and privacy
Discover more in this article about mobile apps and privacy
Which CIO or CISO has not been, at least once, confronted to the pressuring desire of a VIP or a group of young contributors to use their personal apps in the workplace or on their professional mobility tools?
During CyberSecurity International Forum (FIC 2015) held in Lille last January, Pradeo Security Systems’ founding president Clément Saad, while receiving the innovative SME grand prize, explained that “the main threat, which would arise on smartphones and tablets, would be brought through mobile applications, which would then be the interaction point with the digital world”. He added that “a mobile app’s behavior verification, to ensure it’s not collecting your private data” should be done.
Most of mobile apps allow to download all the users’ private data located on their smartphones or tablets. What happens with smartphones and tablets also happens in the connected devices’ world, though the users may not be conscious of it. For instance, do smart watches or jogging armbands (which help joggers to time their running, measure their covered distances and heart rates, etc.) need to have access to the jogger’s full contact list?
How might this be useful to the jogger? If the jogger is a CFO or has responsibilities in an OVI, wouldn’t a random app accessing his full contact list be a little embarrassing? Similarly, these managers would never think of loading the game “Angry Birds” on their workstation, so why should they do it on a professional or a multi purpose mobile phone? What doesn’t seem malicious to one person might perhaps be damaging for the organization the person is working for and might have certain consequences…
To avoid utter prohibition, the firm could provide a single purpose professional mobile phone, independent of the personal cellphone, or change for the COPE (Corporate Owned, Personally Enabled) mode: the device which is owned by the company is containerized to be also used in private mode. It’s then the CISO’s responsibility to block, by filtering, the applications not abiding by the employer’s security policy.