Quick links:
Understanding Part-IS: A New Era in Aviation Cybersecurity
The European Union Aviation Safety Agency (EASA) has launched in 2022 a ground-breaking regulatory framework known as Part-IS (Information Security). This regulation marks a significant step forward in addressing cybersecurity risks within the aviation industry. As cyber threats continue to evolve, Part-IS aims to ensure that aviation organizations implement robust information security measures to protect critical systems and data.
Part-IS in a Nutshell: What Is Important to Remember
The European Union Aviation Safety Agency (EASA) is a regulatory authority founded by the European Union to maintain a high and consistent level of safety in civil aviation throughout Europe. EASA has developed an extensive framework of rules and guidelines that regulate the design, manufacture, operation, and maintenance of aircraft, and oversee the certification of aviation personnel, organizations, and equipment.
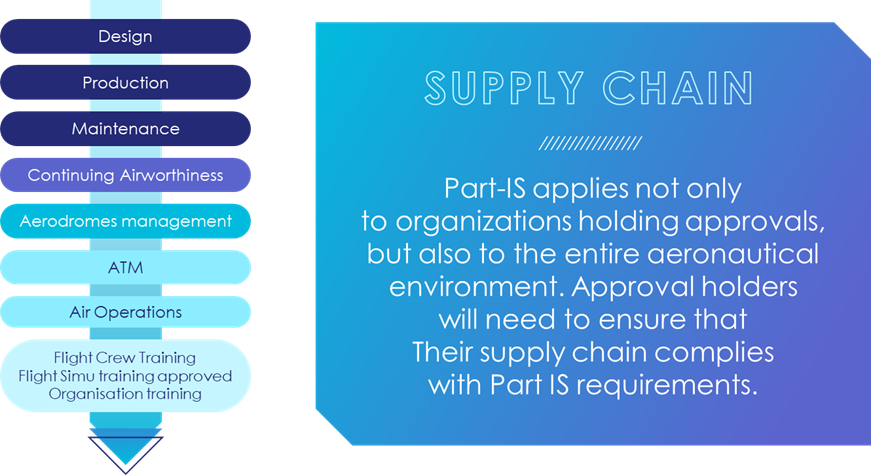
Part-IS is a regulatory framework designed to enhance information security across the aviation industry. It applies to a wide range of stakeholders, including Airframers and OEM but also address airlines, airports, air traffic management (ATM) providers, and maintenance organizations. The regulation focuses on safeguarding aviation safety against cyber threat ensuring the integrity, confidentiality, and availability of information. Part-IS regulatory framework comes in addition to existing approvals, and has to be cascaded to the overall supply chain of organizations holding approvals as long as these stakeholders are contributing to the safety.
The development of Part-IS regulation started several years ago. The initial Part-IS regulations were published in August and November of 2022, while the Acceptable Means of Compliance (AMC) and Guidance Material (GM), which provide more details on how to implement the rules, were only published in July 2023.
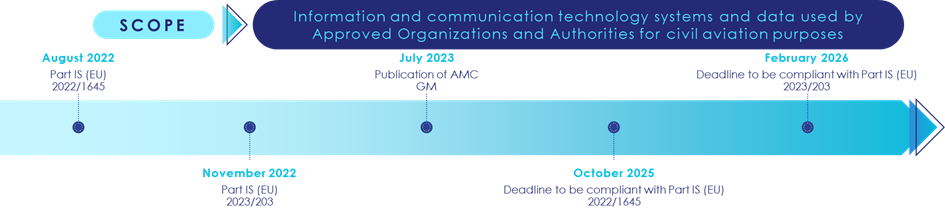
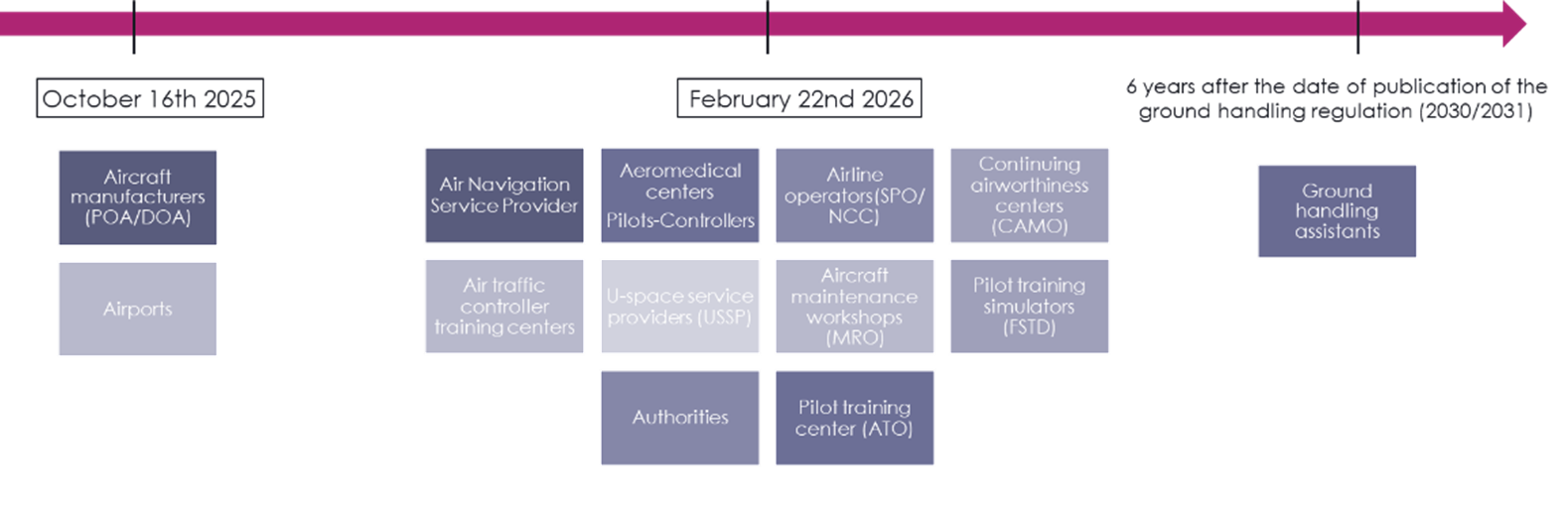 There are several key dates to remember regarding its applicability, depending on the type of organization:
There are several key dates to remember regarding its applicability, depending on the type of organization:
Part-IS is covering a large scope of activities in order to provide confidence that risks having an impact on aviation safety are mastered. Activities required to comply with Part-IS are structured around the 4 following main themes:
- Risk Management: Organizations must identify, assess, and mitigate cybersecurity risks to their operations.
- Security Measures: Implementation of technical and organizational measures to protect information systems.
- Incident Reporting: Mandatory reporting of cybersecurity incidents to relevant authorities.
- Continuous Monitoring: Regular audits and assessments to ensure ongoing compliance and security.
Have you drawn up your compliance roadmap? Steps to Comply Effectively and Efficiently
While Cybersecurity activities are considered since 2006 in systems and Aircrafts development, Part-IS is the first EASA regulation to address cybersecurity to the overall ecosystems. This approach relies on the deployment of an Information Security Management System (ISMS).
As a consequence, addressing cybersecurity risks as expected by Part-IS is a new concern for many stakeholders not originally concerned by cybersecurity activities required by authorities during initial certification process.
Moreover Part-IS comes in addition to already in place requirements coming from authorities to approved organizations. Therefore, not complying with Part-IS can directly affect the approvals already delivered.
Achieving compliance with Part-IS requires a structured and well-planned approach.
Here are the key steps to build an effective compliance roadmap:
- Conduct a Gap Analysis: Assess your current cybersecurity posture against Part-IS requirements. Identify gaps in policies, processes, and technologies.
- Define Roles and Responsibilities: Establish a dedicated team or appoint a cybersecurity officer to oversee compliance efforts.
IT teams, safety teams and management must work together to determine the organization of the ISMS and the roles involved.
This is one of the most decisive stages, as it can completely reorganize the way the organization runs; for example, by getting teams- not used to- talking to each other and to communicate. - Develop a Risk Management Framework: Implement a risk-based approach to identify, evaluate, and mitigate cybersecurity risks.
IT events/incidents need to be assessed in terms of their safety impact, considering IS incident can have an impact on safety. - Implement Security Controls: Deploy technical measures such as encryption, access controls, and intrusion detection systems, alongside organizational measures like employee training and incident response plans.
- Establish Monitoring and Reporting Mechanisms: Set up systems for continuous monitoring of cybersecurity threats and ensure timely reporting of incidents.
- Conduct Regular Audits: Perform internal and external audits to validate compliance and identify areas for improvement.
- Foster a Culture of Security: Educate employees and stakeholders about the importance of cybersecurity and their role in maintaining compliance.
By following these steps, organizations can not only achieve compliance but also strengthen their overall cybersecurity resilience.
Which Challenges have to overcome for achieving compliance?
While Part-IS is a critical step forward, organizations may face several challenges in achieving compliance:
- Complexity of Aviation Systems: The interconnected nature of aviation systems makes it difficult to identify and secure all potential vulnerabilities especially considering that Part-IS is not addressing the products themselves but surrounding activities that could have an impact on products.
- Regulatory Uncertainty: As Part-IS is relatively new, organizations may face challenges in interpreting and implementing its requirements.
- Cultural Resistance: Shifting to a cybersecurity-focused mind-set may require significant cultural change within organizations. The implementation of ISMS can transform the way an organization operates, and it is vital that executive management is committed to these changes, and uses the appropriate means of communication to implement and explain them.
- Evolving Threat Landscape: Cyber threats are constantly evolving, requiring organizations to stay ahead of emerging risks.
To overcome these challenges, organizations should prioritize collaboration, invest in training and technology, and seek guidance from cybersecurity experts and regulatory bodies.

Part-IS as a First Stepping Stone for Cyber Maturity in the Aeronautics Industry
Part-IS represents more than just a regulatory obligation; it is a catalyst for increasing cyber maturity in the aviation industry. By mandating robust information security practices, Part-IS encourages organizations to adopt a proactive and holistic approach for cybersecurity.
This regulation applies not only to the organizations holding approval, but also to their supply chains, which, depending on their criticality and involvement concerning Information System, will have to contribute to to Part-IS requirements.
This lack of maturity in the way to manage the propagation of Part-is can generate burden of work to the overall supply chain supporting approved organization at the beginning.
The introduction of Part-IS marks a pivotal moment for the aviation industry. By prioritizing information security, this regulation addresses the growing cyber threats facing the sector. Organizations must act now to develop a compliance roadmap, overcome challenges, and leverage Part IS as a stepping-stone toward greater cyber maturity. In doing so, they will not only meet regulatory requirements but also safeguard their operations, reputation, and the future of aviation.
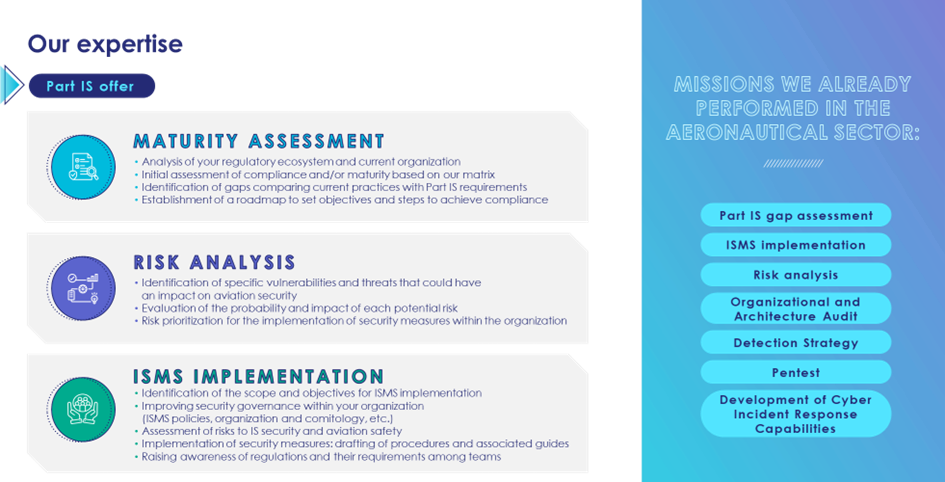
Our know-how
At Thales, we bring unparalleled expertise in compliance with Part-IS regulations, leveraging the synergy between our advanced cybersecurity skills and our deep knowledge of the aerospace sector. We actively work to ensure compliance within our own Thales entities that hold approvals and must adhere to Part-IS regulations. Our expertise has also greatly benefited external organisations by conducting thorough gap assessments, proposing strategic roadmaps, and assisting in the implementation of Information Security Management Systems (ISMS). We are also deeply committed to helping our clients adopt optimal security practices, thereby ensuring their competitiveness and compliance in an ever-evolving environment.