Cybersécurité dans l'espace: comment Thales relève les défis à venir
Understanding the cyber threat:
The Retail industry continues to be a target for financially motivated criminals looking to cash in on the combination of payment cards and personal information. Social tactics include pretexting and phishing, with the former commonly resulting in fraudulent money transfers. Retail is one of the most targeted sectors for cyber-attacks in 2021. The coronavirus pandemic has forced retailers to adapt to survive, regardless of their size. While smaller retailers have moved to card payments and online operations, larger retailers have focused on harnessing big data to achieve efficiencies and maximize profit margins.
This has introduced new threat vectors as retailers’ attack surfaces have expanded, and these vectors are being exploited by cybercriminals keen to steal money and confidential financial information. Data is the new currency for cybercriminals, who focus not just on money and goods but also customers’ personal data that can be stolen and sold online. And with high staff turnover and seasonal workers, retailers face threats from not just cybercriminals, but also insiders.
In 2021:
- 44% of retail organizations were hit by ransomware
- 54% of organizations hit by ransomware said the cybercriminals succeeded in encrypting their data
- 32% of those whose data was encrypted paid the ransom to get their data back
- The average ransom payment was $147,811
- However, those who paid the ransom got back just 67% of their data on average, leaving almost a third of the data inaccessible
- The average bill for recovering from a ransomware attack in the retail sector was $1.97 million
- 56% of those whose data was encrypted used backups to restore data
- 91% of retail organizations have a malware incident recovery plan
![]()
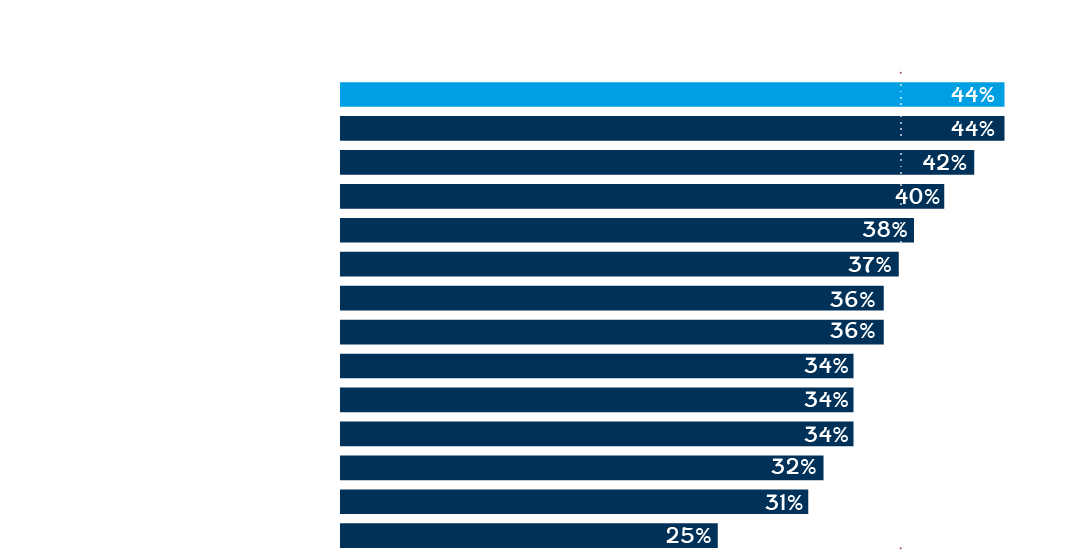
Looking at the prevalence of ransomware across all the sectors surveyed, retail, along with education, experienced the highest level of ransomware attacks: 44% of respondents in these sectors reported being hit compared to the global average of 37%.
Globally across all sectors, the percentage of organizations hit by ransomware in the last year has dropped considerably from last year, when 51% admitted being hit. This drop can be partly explained by the evolution of attackers behaviors.
![]()
Of the 357 respondents across all sectors who reported that their organization paid the ransom, 282 also shared the exact amount paid, including 36 in the retail sector.
Globally across all sectors, the average ransom payment was $170,404. However, in retail, the average ran - som payment was almost $23,000 lower, coming in at $147,811.
![]()
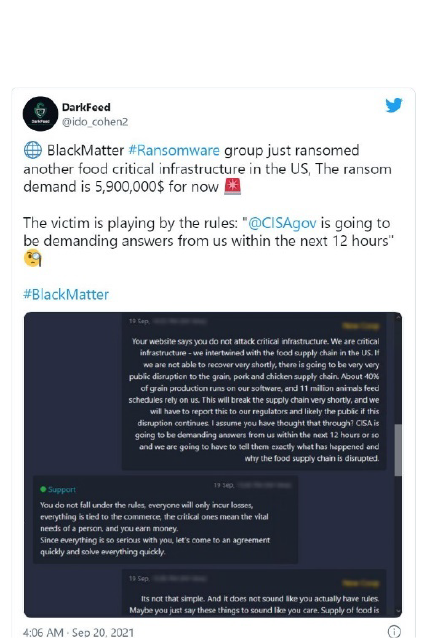
The attack was first discovered after a sample of the ransomware was downloaded from a public malware analysis site.
This sample provided access to the BlackMatter ransom note, the ransomware negotiation page and a non-public data leak page containing screenshots of allegedly stolen data.
Indeed, it is important to show through this attack that when the BlackMatter ransomware first appeared, the attackers stated that they would not target critical infrastructure facilities (nuclear power plants, power plants, water treatment facilities).
From screenshots of the trading page shared on Twitter, the New Cooperative asked BlackMatter why they were attacked as they are considered critical infrastructure and the attack would lead to a disruption in the food supply for grain, pork and chicken.
BlackMatter responded that they did not «fall under the rules» and threatened to double the ransom if the New Cooperative did not change its approach to the negotiation