Quick links:
Implementation of a Cyber risk analysis for an Air Traffic Control Centre
Air Traffic Management (ATM) encompasses all activities aimed at ensuring the safety and fluidity of air traffic. The players in this field are critical operators, whose daily tools rely on information systems that must be secured.
Thanks to their experience in carrying out cybersecurity missions for various international Air Traffic Control centres, including several in Europe, Thales’ cyber teams have developed solid expertise and know-how, the key elements of which will be detailed in this article:
The purpose of conducting a risk analysis for an ATM Air Traffic Control centre
The regulatory framework in the aeronautical sector, particularly for Air Traffic Control
How to initiate a risk analysis and the steps to follow for an ATM centre
Thales’ recommendations for successfully carrying out this type of mission
Genesis of a risk analysis for an ATM system
The ATM system is based on hardware and software components that can be subject to weaknesses, known as vulnerabilities, which create risks and make them potential targets for attacks by malicious actors.
For example, the German Air Traffic Control centre DFS (Deutsche Flugsicherung) saw its office automation system fall victim to a cyberattack in November 2024, and the European aviation regulator Eurocontrol was targeted by an attack on the availability of its website the previous year.
In order to put in place the main security measures adapted to the challenges facing ATM, the cyber risk analysis is the first step in identifying the risks and enabling the ATM centre's risk management department to deal with them accordingly. In addition, the added value of a rigorously conducted risk analysis can be demonstrated to national and international aviation authorities, as well as aviation regulators.
International and European regulatory context for an ATM centre
In this chapter, we will briefly detail the genesis of the implementation of cybersecurity at the legislative level in the international context, and we will see how this legislative context has evolved at the European level.
The ICAO (International Civil Aviation Organization) and its Annex 17
The ICAO was created on December 7th, 1944. This organization governs, at the international level, the rules to be respected by its member states in the field of aviation.
The first requirements in terms of cybersecurity appeared with with Annex 17, drawn up by the ICAO, drawn up by the ICAO, and in particular with the following two founding rules:
The first rule obliges member states to ensure that their air operators identify their critical information and IT systems using a risk analysis, and identify security measures to cover the associated risks (ICAO Annex 17 §4.9.1).
The second rule recommends that member states ensure that air operators have integrated security measures to protect the integrity, confidentiality, and continuity of IT systems and critical data (ICAO Annex 17 §4.9.2).
European Transposition of Annex 17
At the European level, Annex 17 was transposed on September 25th, 2009, in order to clarify these two requirements and to complete them, establishing a basic legislative framework for the implementation of cybersecurity in the European aviation sector.
The European transposition reflects the ICAO rules, of which we detail hereafter a representative sample: in paragraph 1.7, for example, the obligation for the air operator to carry out a risk analysis, draw up an action plan, and implement the associated security measures. In paragraph 11.1.2, it obliges the operator to carry out background checks on staff responsible for physical security, and in paragraph 11.2.8, it requires the operator to train staff responsible for cyber threats.
A New European Regulation for Safety Impacts: Part-IS
In recent years, another European player and regulator has been added to the existing regulations in the aviation sector: the European Union Aviation Safety Agency (EASA).
In 2019, EASA considered that the existing regulations were not sufficient to cover the risks resulting from intentional malicious acts, and wanted them to evolve to take into account all the indirect threats coming from the wider aviation ecosystem, particularly in terms of IT and material supply chains.
The Part-IS regulation focuses on safety impacts in a comprehensive and standardised way across all areas of civil aviation, from product design to flight operations.
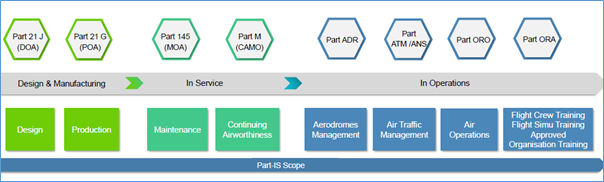
Figure 1: PART-IS regulation scope is covering all civil aviation sectors.
Source: IATA Training Aviation Cybersecurity
Feel free to consult our dedicated article on this topic
In order to comply with these regulations, Thales carries out Cyber risk analyses of ATM systems, using appropriate methodologies (e.g. ISO27005, EUROCAE ED-203A).
In the rest of this article, we show how the standard has been applied in the ATM context.
Starting an ATM Cyber risk analysis
An ATM centre's Cyber risk analysis must start by defining the scope with the ATM centre's management, which has a cross-functional view of all the processes and a decision-making power.
Defining the scope of a risk analysis is essential because all the subsequent stages depend on it.
In general, several workshops are organized with the business teams and ATM centre management to select and specify the business processes and information to be studied in terms of risk. For an ATM centre, we generally find the following business processes:
Air Traffic Services (ATS)
Provides services to avoid collisions between aircraft, various in-flight information to pilots and alerts search and rescue organisations.
AirSpace Management (ASM)
Provides controllers with information for managing and organising airspace to optimise its use by different users (civil, military, etc.).
Air Traffic Flow Management (ATFM)
Provides ATS and pilots with information to balance demand and capacity in the Air Traffic Control system, to optimise traffic flow and avoid overloading sectors or airports.
Calibration (CAL)
Checks the quality of the signal in the airspace and compliance with flight procedures in accordance with ICAO standards.
Continuing Airworthiness of Aircraft (CAMO) / Maintenance Of Aircraft (MOA)
Ensures aircraft maintenance, generally entrusted to an external service provider.
Communication, Navigation, Surveillance (CNS)
Surveillance collects data enabling ATS to know in real time the position, altitude, speed and identification of aircraft in the airspace.
Navigation provides a radio navigation signal to aircraft to enable them to know their position and follow their trajectory correctly.
Communication provides several types of communication:
AMHS (Aeronautical Message Handling Systems) messages via the AFTN (Aeronautical Fixed Telecommunication Network) protocol transmitted to various systems (ATS, MET, ATFM, etc.) and end users (internal and external)
Voice data used between ground-to-ground and air-to-ground communications
Air-ground data link messages (pre-formatted messages exchanged between the controller and the pilot)
OLDI messages exchanged between ATS centres
Aeronautical Information Services (AIS)
Provides the flow of information necessary for the security, regularity and efficiency of international and national air navigation - NOTAM (Notice to Airmen) and SNOWTAM.
Flight Data Procedure (FDP)
Ensures the design of flight paths (instructions to pilots) for aircraft arriving at or departing from a specific aerodrome (taking into account terrain and obstacle data).
Meteo (MET)
Provides weather forecasts, warnings and reports (data is collected from sensors installed in the area outside the airport) and this information is distributed to controllers and pilots
Risk analysis process for an ATM centre
Once the priority business processes and information have been selected and the underlying physical and software equipment clarified, the risk analysis stages are carried out for each of these services, taking into account any interactions between them.
More specifically, the risk analysis stages are based on a dual approach: a compliance-based approach, which checks that the ATM centre's security practices complies with the regulatory standards we saw earlier, and a more consequential scenario-based approach, which examines the impact of potential attacks on the ATM system. The preliminary studies of the business services makes it possible to carry out these stages by following a structural descent, from the business to the technical aspects, while ensuring continuous supervision by management.
For example, the scenario-based approach begins with discussions with management and the business lines to formalise high-level attack scenarios. Since ATM systems are critical, they can be prime targets in national or international conflicts, and the discussions during these stages help to identify possible sources of risk and the impact of potential attacks on ATM systems.
The diagram below is an example of a high-level attack scenario, identified during discussions with Air Traffic Control centre (ACC) stakeholders.
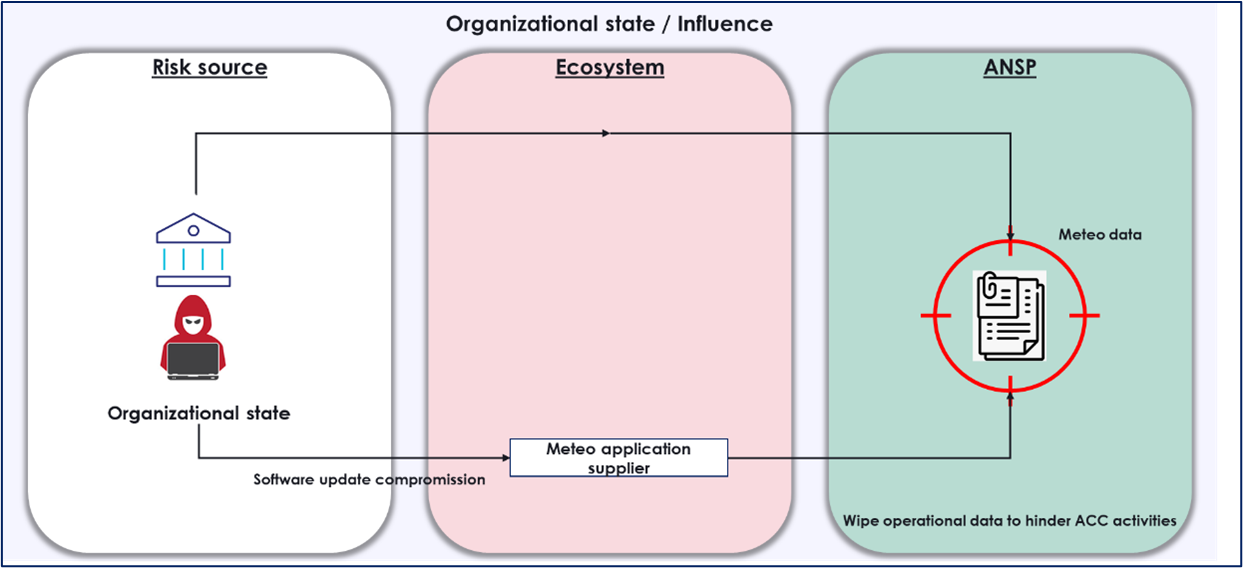
Figure 3: Example of a high-level attack on weather services provided to air traffic controllers via the supply chain
This co-creation not only enriches the analysis process by integrating the specific knowledge of the air traffic control business, but also ensures that the security challenges are better understood throughout the organisation.
Next, it is essential to involve the technical teams to provide a concrete vision of the attack scenarios, through a prism with a more operational scope. This stage focuses on defining the technical modus operandi, identifying potential hardware and software flaws that could be exploited by cybercriminals.
Using the system mapping elements studied with the ATM centre's technical teams - for example, the administrators of the communications servers, or the developers of in-house software used in surveillance - the high- level attack scenarios are translated into concrete paths that an attacker could take within the ATM centre's information system.
The diagram below is an example of an attack scenario with a more operational scope, formalised jointly with the Air Traffic Control Center (ACC) teams, the Meteo teams and the technical administrators of the underlying networks.
Figure 4: Example of an attack on weather services provided to air traffic controllers via the supply chain
In this respect, knowledge of the hardware and software aspects of the information system underlying the ATM, and the expertise of Thales teams in cybersecurity issues, enables the likelihood of the identified operating modes being carried out to be qualified, leading to an initial assessment of the Cyber risk on the ATM system.
Finally, management supervision plays a key role in rating the risks and identifying the appropriate security measures. The results of the analyses carried out with the business teams and the lessons learned from the technical scenarios are used to validate the identification and full assessment of the Cyber risks. This process then initiates a phase of identifying security measures, the implementation of which is studied in collaboration with management - in terms of prioritizing the resources to be allocated - and the technical teams - in terms of technical feasibility.
In short, the synergies generated by exchanges with participants from the various departments in the air traffic control ecosystem (air traffic controller, weather engineer, server administrators, management) provide high added value in identifying and assessing the main risks to the entire ATM system.
Conclusions – Our advice for a successful Cyber risk analysis in the ATM context
To sum up, in the context of ATM, and in order to generate satisfaction, risk analysis must be carried out taking into account the elements detailed below.
Firstly, it is absolutely essential at the outset to properly define the scope with management, and in particular to precisely define all the business processes and information that need to be taken into account in the analysis.
In addition, the ATM centre's management team as well as the regulatory and risk management departments must be included in the study, and it is important to obtain their validation of each stage before moving on to the next.
In order to take account the Part-IS regulation, which focus on safety risks, we recommend clearly highlighting the safety impacts and separating them from the other usual impacts that we are used to representing for traditional IT systems, i.e. operational, financial, legal or image impacts.
Example:
If the centre's ASM (Air Space Management) business service no longer works (the availability criterion is impacted), then the air centre will be unable to allocate airspace in the case of a military exercise, for example. The operational impact would be critical, but there would be no safety impact.
If, on the other hand, the voice communications between the ground and the pilot are spoofed and modified (the integrity criterion is affected), then the pilots will receive incorrect information. The safety impact will then be critical.
This approach will enable the ATM centre to transmit the safety-related risks to the National Aviation Authority in accordance with Part-IS regulations.
Another important point, in order to give real value to the risk analysis carried out, is to take into account any Cyber technical tests carried out on the perimeter studied. The results of these tests and any concrete attack scenarios that may have been uncovered should be taken into account. The risk analysis can then be completed and additional attack scenarios added, or the likelihood of the initial scenarios reassessed, either upwards or downwards.
In conclusion, an ATM centre’s risk analysis must be reviewed regularly to take into account new updates to the centre’s IT elements (air traffic control software, weather applications, changes to regulations, new cyber threats in the aviation sector as a result of the geopolitical context).
This regular updating will enable the ATM centre to keep its risks under control, to be able to justify an up-to-date action plan to the National Aviation Authority and to reassure all the ATM centre’s partners, such as other centres in neighbouring countries or the European regulator.
Mastering Cyber Risks in ATM: Relying on the Expertise of a Trusted Partner
Risk assessment is an essential step to strengthen the resilience of ATM systems against growing threats, particularly those related to cybersecurity. In this context, relying on an experienced partner who possesses knowledge both in the specificities of the ATM domain and the requirements of cybersecurity becomes a true asset. With recognized expertise across the entire Cyber value chain—from risk assessments to the deployment of solutions and protection services—Thales has been supporting over 50 Air Navigation Service Providers (ANSPs) and Civil Aviation Authorities (CAAs) worldwide in their security efforts for more than 10 years.
Jean-François TYRODE

Jean-François is a highly experienced professional who has been working within Thales for 20 years. He currently serves as Mission Director in the Cyber Consulting Department of Thales Cyber Solutions. Since 2017, his primary focus has been on performing risk analysis and cyber assessment for the ATM (Air Traffic Management) environment. His extensive experience includes working with multiple customers in various countries, which has earned him strong customer references in the field of Cyber consulting.
Jean-François holds several certifications including ISO 27001 Lead Implementer, EUROCONTROL/Cyber, and IATA/Cyber. He is also certified in risk management. These certifications reflect his expertise and proficiency in implementing information security standards and frameworks.
Tristan LISCIA BEAURENAUT

Tristan is a cybersecurity consultant with several years' experience at Thales.
He focuses on governance and security architecture. In particular, he specialises in the analysis and management of Cyber risks.
His experience has led him to contribute to projects for French and international clients in a wide range of sectors, including aeronautics, energy, defence and banking.
He currently holds a number of certifications, including ISO27001 Lead Auditor and Lead Implementer. He is also certified in risk management, and is qualified by the French Information Systems Security Agency (ANSSI) to conduct audits.



