From delegation to collaboration: unlocking the full potential of Managed Security Services (MSS)
Strengthening cybersecurity: balancing in-house expertise and specialised support
As the world and business operations become increasingly digital, organisations face an exponential rise in exposure to cyber threats. Just as having departments for human resources, finance, and operations is essential, every business must also prioritise a clear and proactive strategy to safeguard its information and other assets. Cybersecurity is no longer optional - it is a fundamental aspect of sustaining business continuity and protecting reputation.
While building an in-house team of IT and cybersecurity professionals is a common approach, it may not always be the most efficient or effective solution. Engaging an external provider for Managed Security Services (MSS) offers a strategic alternative by outsourcing the responsibility for your organisation’s security. This approach decreases the need for directly employed staff, allowing businesses to access specialised expertise and scalable solutions without the overhead of recruiting, training and maintaining an internal team.
Outsourcing cybersecurity to an external company with expertise in a broad array of cyber services can offer several significant advantages. Highly specialised professionals bring comprehensive expertise, a broader perspective on possible cybersecurity strategies to grow in maturity, and up-to-date knowledge of the ever-evolving threat landscape. Drawing on their experience across multiple customers, such specialised firms mutualise expertise. They provide access to cutting-edge tools and techniques and allow your internal IT team to focus on core business activities.
Furthermore, specialised cybersecurity firms possess advanced threat intelligence capabilities. Thanks to their collaboration with Threat Intelligence communities worldwide, they have access to the latest information on current threats. Please refer to our article on the subject: “Enhancing Cyber Defence with Threat Intelligence in CSOC”.
Finally, specialised firms are up-to-date with the latest regulatory requirements and can ensure that a company remains compliant with relevant laws and standards, reducing the risk of legal issues and fines. They also make sure to obtain relevant certifications for themselves (like ISO27001) and adhere to industry standards to reinforce trust by assuring clients that the services provided meet stringent benchmarks.
Service Management: the backbone of Managed Security Services
Service Management is the foundation that ensures the successful delivery of Managed Security Services (MSS). Rooted in principles derived from industry frameworks like ITIL (Information Technology Infrastructure Library), Service Management provides a structured approach to designing, implementing, and continually improving services.
As its core, Service Management emphasizes consistently delivering high-quality services. This includes proactive guidance on emerging technologies, robust threat detection, timely incident response, etc. By demonstrating excellence and leadership in service delivery, providers can instil confidence in their clients and build a strong partnership.
A comprehensive Cyber Service Catalogue typically encompasses the following key pillars (from NIST CSF):
◾ Identify and Assess: Recognise vulnerabilities and evaluate risks - Vulnerability Assessment (VA), Threat Expose Management (TEM) and Cyber Threat Intelligence (CTI).
◾ Protect and Prevent: Implement measures to reduce the likelihood of threats, incl. Security Technology Management (STM).
◾ Monitor and Detect: Continuously watch for suspicious activities and identify threats - Managed Detection and Response (MDR).
◾ Analyse and Respond: Investigate incidents and respond to minimize impact - Digital Forensics and Incident Response (DFIR).
◾ Recover and Learn: Restore operations and implement lessons learned to strengthen defences.
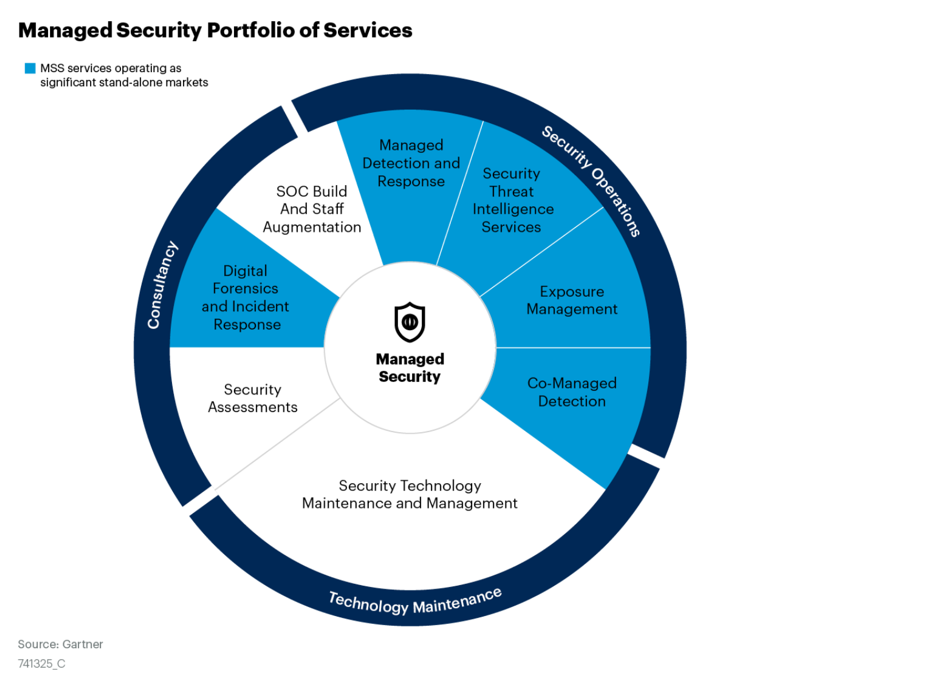
Governance and Service Management (GSM) provide the support structure for these functions, ensuring they are executed effectively and consistently. At Thales, Service Management is entrusted to the Projects & Services Management team, responsible for the seamless execution of MSS contracts. Each client is assigned a dedicated Service Delivery Manager (SDM) whose role is pivotal in ensuring the transparent delivery of subscribed services within agreed Service Level Agreements (SLAs). The SDM acts as the primary point of contact for the client, maintaining strong relationships, collecting feedback, and proposing enhancements to service delivery. They are responsible for regular service reporting, analysing and evaluating key performance indicators (KPIs) to ensure services meet contractual standards. They ensure appropriate expertise and availability are assigned to fulfil service obligations, chair Service Review Meetings, and ensure clear communication of updates, procedures, and action plans.
The ultimate mission of the SDM is to maintain and enhance client satisfaction. By acting as the client's primary liaison within Thales operational teams, the Service Manager ensures that the MSS partnership thrives, evolving with the customer’s business needs and continuously delivering value.
Reporting is the cornerstone of MSS
Reporting is a fundamental element of managed services, serving as the cornerstone for transparency, accountability, and continuous improvement.
Comprehensive reporting is essential for building trust between clients and their managed service providers. It assures clients that the services entrusted to the provider are being managed effectively and delivering measurable value. While no cybersecurity operation can guarantee 100% protection against attacks, implementing multiple layers of security significantly reduces the overall risk to organizations.
Regular, detailed reports provide crucial visibility into key metrics such as incident resolution times, system performance, threat detection rates, and compliance adherence. Moreover, these reports serve as valuable tools for the client’s Security and Risk Management Leaders, enabling them to integrate the insights into the organization’s broader cybersecurity strategy. By using this information strategically, clients can enhance their defences and ensure that senior management, who bear ultimate responsibility for the organization’s security, are well-informed and equipped to make critical decisions. In this way, reporting not only strengthens the partnership between the client and provider but also reinforces the organization’s overall security posture.
Finally, reporting meetings (Service Review Meetings) serve as vital opportunities for collaboration and the exchange of critical information. These sessions provide a platform to discuss ongoing threats, emerging trends in the market, and the progress of key initiatives such as penetration tests, audits, and disaster recovery plans. These meetings foster a productive dialogue between the client and provider, ensuring alignment on priorities and strategies, and strengthens the overall partnership.
Service Delivery Management applied to SOC Countermeasures
The primary role of the Security Operations Centre (SOC) is to monitor the customer’s IT systems for suspicious activity and alert them to potential threats. When an anomaly is detected, the SOC follows established escalation paths to inform the customer, who then determines whether the flagged activity represents a true positive (an actual incident), a benign true positive (correctly flagged but legitimate or controlled activity), or a false positive. One of the most common remediation actions is blocking an IP address on the firewall or other security tool. However, for straightforward scenarios or situations requiring an immediate response, customers are more and more interested in active countermeasures from the SOC. This allows the SOC to take predefined actions, such as blocking malicious activity, without waiting for customer intervention, significantly reducing response times and mitigating risks more effectively.
The implementation of active countermeasures requires careful consideration and alignment between the SOC and the customer. This is where the Service Delivery Manager (SDM) plays an important role. It is the SDM's responsibility to engage customers in discussions about enabling such countermeasures, ensuring that they understand the benefits, risks, and prerequisites involved. These discussions include defining clear rules of engagement, specifying the types of actions the SOC is authorized to take autonomously, and establishing robust governance around these activities. The SDM must also facilitate the creation and integration of relevant procedures, such as defining escalation paths for scenarios requiring immediate action or customer intervention. By fostering collaboration and ensuring alignment on these measures, the SDM helps build a more integrated incident response framework.
Customer responsabilities in building a strong collaboration
When clients delegate security responsibilities to an external provider, establishing trust in the provider's ability to manage critical aspects of their operations is paramount. However, trust alone is not enough - clients must take an active role in laying the foundation for a successful partnership. This begins with the customer’s responsibility to establish robust management practices and implement effective Information Security Management System (ISMS) processes. These measures enable clients to clearly define objectives and identify the risks to be addressed by the provider. The external service provider can support that process, but the client should maintain full control over the responsibilities being outsourced.
The external provider should act as an extension of the client’s internal teams. To ensure this partnership operates effectively, clear and open communication must flow in both directions. Clients need to provide its service provider with essential information about their operational context, objectives, and risk landscape. It means that some classified documents like audit reports, penetration testing reports, network diagram, past incident reports or other sensitive information could be shared (in a secure way) with the provider.
Additionally, integrating outsourced cybersecurity functions with existing internal processes is critical for achieving cohesion and operational efficiency. Clients must establish complementary procedures and organise their internal teams to align the managed services with their organisational practices. This is especially true for Managed Detection and Response (MDR) services within an external Security Operations Centre (SOC).
The SOC is just one building block among many. Governance, risk analysis, and protective and detective tools all play a role in creating a robust defence strategy. A SOC’s effectiveness depends not only on its ability to detect and respond to threats but also on the collaboration and preparedness of the client’s internal teams. If calls are ignored by the customer, ongoing attacks might go unnoticed or noticed too late. To maximize the value of MSS, customers must allocate dedicated internal resources to collaborate with SOC activities, manage incidents and investigate threats.
Achieving a strong partnership requires the development of integrated procedures, such as:
📌 Interpret vulnerability scan results frequently: Assess and prioritise vulnerabilities reported by the provider.
📌 Regular review and resolution of pending escalated alerts: Evaluate and respond to alerts flagged as high-priority or requiring client action.
📌 Investigating alerts based on different detection scenarios: Define playbooks or manuals outlining investigation protocols for different threat detection scenarios to ensure consistent responses by internal teams.
📌 Implement first-response actions: Outline remediation steps for each incident type, ensuring rapid containment and mitigation.
📌 Defined steps for activating CSIRT in the event of an incident, including roles, responsibilities, and points of contact; Acting upon recommendations following the yearly Incident Response Preparation exercise.
These procedures must be well-documented, accessible, and familiar to internal teams to ensure seamless operations during critical moments.
By maintaining control over these aspects and collaborating closely with the provider, clients ensure that the partnership aligns with their strategic goals. This integrated approach not only enhances the effectiveness of the MSS but also strengthens the client’s overall cybersecurity posture.
In a nutshell
By fostering open communication, setting clear expectations, and implementing regular controls, the client and provider can build a strong, collaborative relationship. This partnership allows the client to concentrate on their core business activities while relying on the provider’s expertise to address complex and evolving security challenges. Together, they can develop a resilient security strategy that aligns with and supports the client’s broader business goals.



