Wallix in OT: How to secure accesses and connections to industrial environments (OT)?
Introduction
In today’s digital landscape, securing access to both IT and OT infrastructures is critical. As cyber threats increase, organizations need solutions that provide secure and controlled access to their most sensitive systems.
The goal of this blog post is to give you a clear overview of Wallix Bastion, a Privileged Access Management (PAM) solution, and how it can be integrated into both IT and OT environments. We'll take a closer look at its powerful Universal Tunneling feature, which is especially useful in OT environments.
This post is intended to provide a basic understanding of the solution. Detailed configurations will not be covered here. For those looking to dive deeper, please engage in a chat with us. Also, a talk will be held by Thales and Wallix on September 19th at the Cyber Meet-Up 2024 event.
Quick Recap - What is the Wallix Bastion ?
Before we jump into how Wallix Bastion applies to OT environments, let’s quickly recap what it does in general, for both IT and OT.
Wallix Bastion is a powerful PAM solution designed to manage and secure privileged access to critical systems. It offers strong security features like:
Access Control: Only authorized users can access privileged sessions on sensitive targets through granular and flexible authorization policies, ensuring that no unauthorized personnel can gain access to critical systems.
Session Management: Wallix Bastion supports a wide range of protocols, allowing it to connect to various devices and systems, from IT to OT. You can manage RDP, SSH, VNC, RLOGIN, and TELNET sessions, making it compatible with a diverse array of devices.
Password Management: Credentials are securely stored and automatically rotated by Wallix Bastion, ensuring that passwords are never exposed to users.
Auditing: Wallix Bastion offers extensive auditing capabilities. Each session is live video recorded, and all user actions are fully transcribed into text, allowing for detailed post-session review. It also logs essential session details like start time, end time, and duration, ensuring that every access event is tracked for compliance and security purposes.
OT Compatibility: One of the standout features for OT environments is Universal Tunneling. This feature leverages SSH tunnels, NAT, and port forwarding to create the secured tunnel and control OT devices securely.
Scenario - IT Admin Secure Access to a Windows Server via RDP
To help you to understand how the Bastion architecture works, let’s take an example: a system administrator needs to access a Windows Server via Remote Desktop Protocol (RDP).
- The IT admin logs into the Wallix Bastion web interface using his standard account.
- The Bastion displays all the sessions the admin is authorized to access.
- The admin selects the session he wishes to connect to.
- The admin opens an RDP file, which contains a one-time password (OTP) valid for a few seconds. This OTP allows them to initiate to the session via a secure tunnel, with all traffic routed through the Bastion.
- The admin now has their session open with his privileged account. The entire session is monitored and recorded.
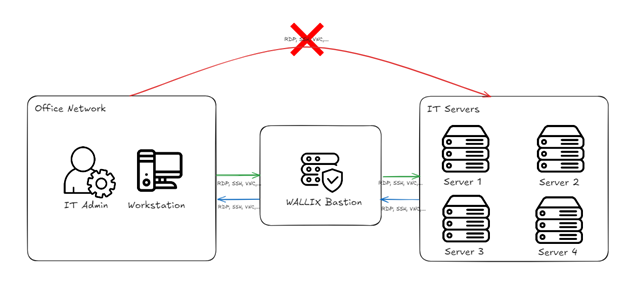
Figure 1. Example of basic architecture for this use-case
Of course, while the Bastion architecture is highly effective, it’s not magic. The security it provides relies on proper coordination with firewall rules that block direct access from the Office Network to the IT servers, ensuring that all sessions are initiated and managed through the Bastion as a proxy.
In this example, we’ve focused on an RDP session, as it’s the most common use case we encounter, but other protocols are fully supported as well, including VNC, SSH, RLOGIN, and more.
Auditing of the session
For RDP sessions, Wallix Bastion provides a full text transcript of the session, which can be downloaded as a CSV file. Auditors can also view live sessions and generate an MP4 video recording of the session for later review. Additionally, they can request access to ongoing sessions with the user’s approval.
Note: These auditing capabilities are available for other protocols like SSH, VNC, and Telnet as well.
Now let’s dive into how Universal Tunneling takes it a step further in OT environments.
Deep dive into the Universal Tunneling
Universal Tunneling is a breakthrough feature designed for OT environments. It provides a secure, encrypted tunnel over SSH, ensuring that industries managing critical infrastructure - like power grids and manufacturing systems - can securely access their OT systems.
What makes Universal Tunneling so powerful is its simplicity of use. With just a few steps, users can quickly create privileged sessions by encapsulating any OT protocol within the SSH tunnel. This allows technicians to access OT devices securely, directly from their workstations, without exposing sensitive systems to unnecessary risks.
Scenario: Universal Tunneling to contact SCADA webserver in the OT Environment
Let’s say a technician in the Office Zone needs to access a SCADA web server located in the OT Zone. SCADA systems are used to control and monitor industrial processes, so securing access is critical.
- The IT admin logs into the Wallix Bastion web interface using his standard account.
- The Bastion displays all the sessions the admin is authorized to access.
- The admin selects the session he wises to connect to.
- The admin downloads and open a “.puttywab” file, which is designed to be opened with Wallix Putty: a modified version of Putty developed by Wallix to use OTP (One-Time Password). You can find the GitHub repository here or download it directly from the Wallix Bastion.
- The session is now open with port forwarding and NAT configurations (if needed) already set up, allowing the admin to access the SCADA web server directly from their browser.
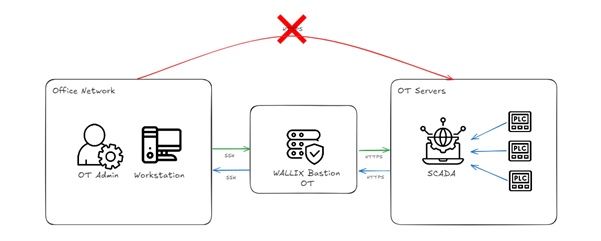
Figure 2: Illustrative schema showcasing the flow from the Office Zone to the OT Zone through HTTPS, encapsulated by Universal Tunneling.
This basic setup provides a simple, foundational model for understanding how Universal Tunneling works.
Scenario: Universal Tunneling for Direct Communiation with an OT Zone MQTT Broker
Modern OT environments rely heavily on protocols like MQTT for communication between sensors, controllers and Cloud analytics. But how can you allow external devices to securely communicate with an MQTT broker in the OT Zone without exposing your OT network to risks?
With Universal Tunneling, it’s simple:
- Establish the Tunnel: The technician uses Wallix Bastion to create a secure SSH tunnel to the MQTT broker.
- Port Forwarding: The MQTT port is forwarded from the technician’s machine to the broker in the OT Zone, keeping all data encrypted.
- Direct Data Flow: Once the tunnel is active, MQTT messages can be sent and received securely, from the user’s workstation favourite MQTT client to the MQTT broker, without exposing the OT network to unauthorized access.
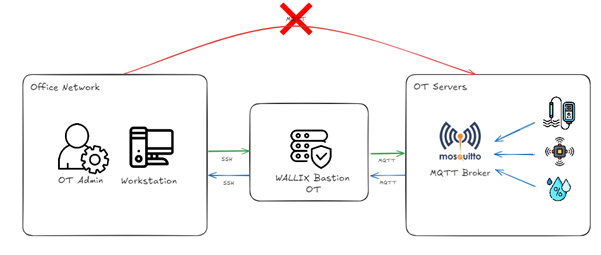
While the two OT scenarios may seem different - the first involving access to a SCADA web server and the other setting up a tunnel for MQTT flows - they are actually very similar and simple to set up. The only difference is in the port being configured to be forwarded, which is configured in the Wallix Bastion tunnel setup.
What about the auditing of these specific sessions?
While users access OT systems via Universal Tunneling from their own workstations- which are not directly audited by the Bastion session probe - certain limitations apply. For instance, it is not possible to generate a live video recording or session transcription in this setup.
However, Wallix still offers basic session auditing details. You can monitor key details, such as the start time, end time, and duration of each session. To provide more insights, the auditor car downloads a pcap file for the entire session.
A pcap file (packet capture) is a detailed recording of all network traffic during a session. It allows you to analyze network activity in-depth by examining the packets exchanged between the user and the OT system. Using tools like Wireshark, you can inspect these files to understand exactly what occurred during the session, such as commands sent, data exchanged. This provides a detailed forensic trail even when live video recording or transcription isn’t available.
Let's going further
To extend the auditing and monitoring capabilities of Wallix Bastion, consider automating the analysis of pcap files. You could create a bash or python script to download these files automatically and use tools like tshark to log, monitor, and alert on specific actions via a SIEM integration.
I have deliberately omitted details on Wallix Access Manager in this post. This solution offers a range of features beyond auditing and monitoring, including enhanced remote access capabilities. It serves as a tailored VPN for accessing Wallix sessions from outside the company LAN and simplifies remote usage with additional features. This topic warrants a separate blog post for a thorough exploration.
For both OT and IT environments, you can also configure Remote Apps within Wallix Bastion. This setup provides full control and auditing for fat clients (desktop applications), offering a viable alternative to basic sessions or Universal Tunneling, depending on the context and architecture of your applications.
Wrapping up
This blog post aimed to provide a general overview of Wallix Bastion and its integration into OT environments, using easy examples to simplify the concepts.
Wallix offers a broad range of other capabilities beyond what was covered here. Additionally, many features can be further customized or scripted to meet specific security and compliance needs.
If you’re interested in a deeper dive into Wallix and its OT and IT solutions, including Universal Tunneling, don’t miss the Cyber Meet-Up 2024 event on September 19, where a detailed conference will be held by Thales and Wallix together.
Thank you for reading. Feel free to reach out if you have any questions or wish to continue the discussion.



